Introduction:
The software Folder Lock is not just restricted to the basic encryption and locking of files and folders. In broader terms, it has improved to be a complete data security solution that lets you get rid of files that you no longer need using shredder, create a backup of your files on the cloud, store banking details in protected password wallets and more. All such features were implemented as per the user’s feedback to produce an even better version of Folder Lock.
How To Protect Your Files & Folders From Hackers With Folder Lock?
Folder Lock does not allow hackers to access your protected files and folders, even if they access your hard disk using special tools. Furthermore, Folder Lock with its Virtual Keyboard prevents all possible key-logging tools that might be running on your computer for monitoring your keystrokes. Since no keystrokes will be pressed, you can be sure that the password you enter through Virtual Keyboard is safe from key-logging attempts. To access Virtual Keyboard, click on the Virtual Keyboard button right next to every password field.
Folder Lock features enhanced security protocols in the form of Hack Security. Hack Attempt Monitoring feature helps maximize protection of your data against hacks and helps you to Protect Your Files And Folders From Hackers With Folder Lock. The Hack Monitoring setting sets certain triggers for Folder Lock to either Exit Application, Log-Off Windows, or System Shutdown upon hack attempts.
Hack Security provides you with the settings that provide options to view Incorrect Password Logs and Activate Incorrect Password Actions. With Folder Lock, you can restrict access to the program in the ‘Hack Security’ tab in ‘Settings. Once you’re inside the ‘Hack Security’ tab, you can then set security parameters for application behavior upon a certain number of incorrect password attempts. You can set the program to Exit Application, Log Off Windows, or Shutdown Windows. This security option enables you to view, monitor, and set specific actions to be performed based on any hack attempt. In this option, you can not only view Incorrect Password Logs (including the time of attempt, date of attempt, and application area where an incorrect password was attempted) but also set Incorrect Password Action.
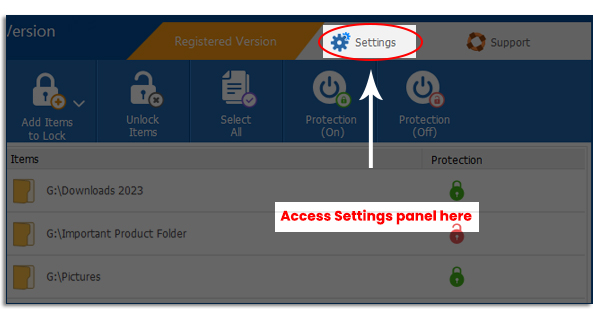
To check if someone has tried to hack into your passwords, simply run Folder Lock and go to the ‘Settings’ panel (see image below).
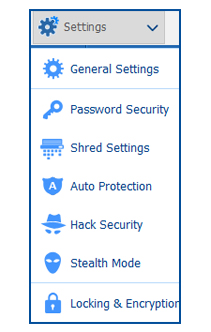
After clicking on the Settings button, click on the Hack Security button as shown in the image below.
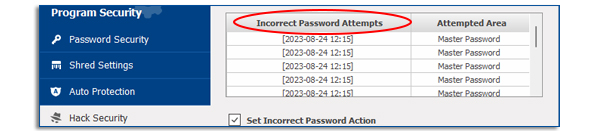
Once you are in the Hack Security tab inside the Settings panel, you can then view the ‘Incorrect Password Log’ in the hack Security tab, which will display details on incorrect password attempts and the program features where the incorrect passwords were attempted. (see image below).
Please remember that Hack Security is in the Program Security tab within the Settings panel. The Program Security has a special security setting that requires you to either enable or disable an option in the security password settings. (see image below).
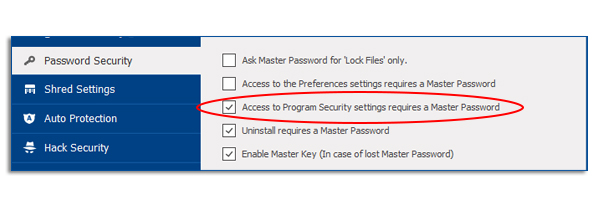
If you have enabled this security option, then upon accessing the Hack Security tab in the Settings panel, you will be required to enter the Master Password. (see image below).
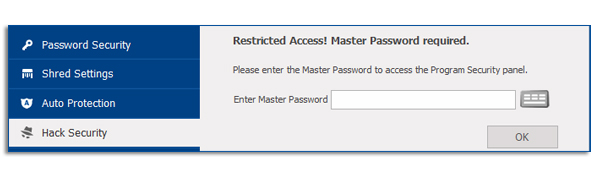
Enter the Master Password if you see the above screen, and click on ‘OK’ to continue. If you have not set the Master Password requirements for Program Security settings tab, then you will be taken straight to the Hack Security tab without seeing the above screen.
Incorrect Password Action is a security parameter, when once activated, will perform the following tasks, after a specific number of incorrect password attempts, to thwart any further possible hack attempt. (see image below)
- Exit Application: When this option is selected, the application will close
- Log-off Windows: This option will log off the user from his Windows session
- Shutdown Windows: This option will shutdown Windows
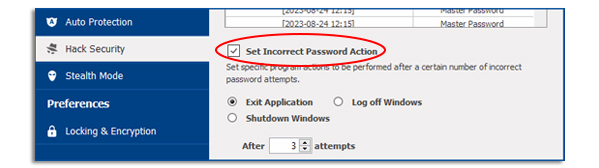
Set your preferred setting for the Hack Security setting and then click on ‘Apply’ to confirm the changes. Once you have completed and confirmed the changes made, you can then simply click on the ‘OK’ button to exit the Settings panel.
You now have maximized security by enabling an active data monitoring system right within Folder Lock.
Conclusion:
With the addition of Folder Lock’s hack attempt feature along with other essential features, Folder Lock continues to be one-step ahead of the people who you do not trust. Although there is less or no chance in saying that the hackers would one day find an end to their doings, but until then, it is mandatory for us to lookout for data ourselves in order to avoid any data thefts or similar attacks.
