With the recent events unfolding over the state of data security or rather the lack of it in most instances is good indication of how even big organizations can be susceptible to the risk of data breach.
Data breach incidents like the one involving Sony Corporation and SEGA only goes to show the vulnerabilities in the system which is otherwise considered well guarded.
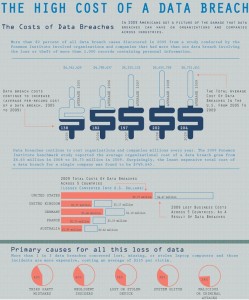
Since most of these incidents involved penetrating security systems and accessing confidential information by using basic hack methods, the focus is on protecting data and information at a fundamental level. Take the recent data breach incident at the Texas State Comptroller’s office for example. The incident exposed sensitive data on some 3.5 million residents.
In another incident, as reported in Austin’s KUTNews blog site, “As many as 4,900 current and former employees of the Texas Department of Assistive and Rehabilitative Services (DARS) may have had their personal information exposed in the latest data security breach involving state workers.” And even though much of the incident event details were not divulged to the public, from where the affected individual stands, the distinction between exposing only a name and address, or exposing more sensitive personal details like drivers license, Social Security, credit card data, etc. is wide and ever expanding.Organizations affected by such attacks need to take a much more in-depth look at their current network security and data protection mechanism. The hack collective – Anonymous and LulzSec – are having a field day taking down Web servers and breaching network security and retrieving confidential information left, right, and center.Tight security means impenetrable data protection system that employs robust tools to either prevent sensitive data from being saved or transported on portable storage devices or encrypting such data and information even if systems are breached. Adding strength to such systems should be the systems’ capabilities to monitor incoming as well as outbound traffic, log on attempts, wrong password attempts, automatic system shutdown and lockdown and such to ensure sensitive data does not leave the computers, laptops, and networks.A comprehensive data protection policy needs to look at a holistic data protection system that provides government-grade encryption (128-bit; FIPS 197), data locks, files and folders protection, encrypted passwords, digital footprint evidence removal, computer or laptop activities removal, permanent data remanent or data removal mechanisms, and secure backups in the form of encrypted online accounts to store data and information.
This comprehensive approach to providing data protection is the means of ensuring that your data as well as customer data is kept safe and secure at all times (End-to-End) from corruption and that access to such protected data and information is suitably controlled and monitored. It is then only fair to conclude that data security under these terms helps to ensure privacy as well as protection of personal, confidential, sensitive, and top secret data.
Whether the data breach incident has Robin Hood element to it (ref. Anonymous & WikiLeaks vs. The World) where the hacker collective fights for free Internet, or when the incident involves an actual hack aimed to hurt ( ref. Epsilon, RSA Security, Sony), the situation is gruesome in the least. And since data breach events seem to have gotten out of control (hack collective LulzSec and Anonymous are responsible for almost most of the biggest data breach incidents over the last few months), it seems the critical moment of truth for securing data is here and now.
As mentioned earlier, there is so much more that organizations need to look at a comprehensive solution to data protection. And since there is no such thing as an impenetrable protection, it would be unfortunate to be a victim of such an incident mainly because the security experts were too busy impressing their bosses and saving costs on securing data.
These attacks don’t seem to be taking any prisoners. Data security should look into a similar strategy.
The Encryption Element
To implement such a strategy, the data security solution must have software based encryption of data to prevent any incident of data theft or data leakage.
Portable Data Protection
If a malicious program or a hacker tries to corrupt the data to make it unrecoverable or unusable, strong portable data protection safeguards is a must to complement encryption.
Another aspect of data breach may involve gaining access to the operating system through USB drives and may be used to spread malicious programs, making the system unusable. For such a scenario, the solution must include an access-driven data protection mechanism that will either completely block all access to the computer or laptop, or block certain features and functionalities. Such a security solution can help prevent read and write access to data, ensuring very strong data protection against data leakage, corruption, tampering, and overall unauthorized access.
The world is creating a lot of data. Realistically, this means “1.8 ZB (Zettabytes) being created and replicated (as in copied to DVDs and shared in the cloud) this year alone” (Mashable, 2011), which would require 57.5 billion 32 GB iPads to store, which is about $34.4 trillion worth, which is a figure equivalent to the GDP of the United States, Japan, China, Germany, France, the United Kingdom and Italy combined. These figures are an indication of how much data we’ll create and store just this year of 2011. Online backups of such data thus require a strong solution that is based entirely on data protection.
Backups, generally, are used to ensure that data which is lost can be recovered at a later time and at a different location if need be. The ability to provide this solution is critical to a comprehensive data security solution.
The charm of online storage accounts that provide personalized digital storage boxes rely on its security features. The security provided include 128-bit or 256-bit SCG encryption at minimum and requires further authentication protocols that match hardware IDs as well as basic personal information. A minimum of two-way authentication is common amongst more robust online storage solutions.
Hidden Data OR Data Masking
Hiding critical data from unauthorized access is an integral part of a comprehensive data protection solution. This ensures that certain data and information that need to be stay protected in out for view for unauthorized users and program access. Files, Folders, program files (.EXE) can all be hidden and protected from any potentially malicious user.
Data Remanent Removal OR Data Shredding
An overwriting mechanism that permanently removes data traces left over after erasing or deleting data form PCs or laptops or USB drives. This mechanism should at minimum provide government level data removal methods to ensure maximum protection of privacy as well as the data elements.
Encryption
Wikipedia defines encryption as “the process of transforming information (referred to as plaintext) using an algorithm (called cipher) to make it unreadable to anyone except those possessing special knowledge, usually referred to as a key. “ Encryption can be used to protect files anywhere where it resides, for example on the computer or on storage devices such as the USB flash drive.
With the number of data breach incidents that have exposed customer data through loss or theft of laptops or backup drives, the role of encryption in the overall context of data security is ever so clear and important. Files, folders, drives, as well as portable data can all be encrypted to protect them in the event any existing physical security measures fail. Portable data encryption comes under the domain of Data-in-Transit, and encryption is also used to protect data that is constantly in transit, for example data movement over the Internet.
Encryption is also widely preferred for email attachments or online transactions as encryption can take care of protecting the confidentiality of messages. Any interception, if successful, can only intercept the email messages and will not be able to decipher the actual attachment in the email. Further measures that improve protection of messages focus on the integrity and authenticity of a message (e.g. digital signatures).
Mobile Data Protection
Most hardware manufacturers for the mobile industry fail to integrate built-in protection of data on mobile phones. The age of mobile telephony, social connectivity, and mobile purchases is upon us with full force. The amount of data exchanged over mobile phones is gargantuan, but due to hardware manufacturer’s negligence, most mobile devices do not come equipped with user-controlled encryption or digital signature capabilities. In such situations, having a software based encryption solution for mobile devices is paramount to stay connected and protected even when you’re on the go.
International Standards
Data security is covered under the Information Security category in The International Standard ISO/IEC 17799 records. Its most essential component principle states that all stored information and data should be owned, whereby the responsibilities that lie with the owner is clear and concise in terms of who is to protect and control the access to that data.
Why Is Data Security Important Now More Than Ever?

Data security is important now more than ever because of the increasing amount of data being stored and shared online. With the rise of cloud computing, companies are storing more data than ever before, and this data is vulnerable to breaches and cyberattacks. Data security is important to protect confidential and sensitive information, such as customer data, financial data, and intellectual property. Data security is also important to protect companies from data breaches, which can lead to significant financial losses and reputational damage.
What Is Security And Why Is It Important?
Security is a set of practices and technologies designed to protect data, networks, systems, and other resources from unauthorized access, misuse, and damage. Security is important because it helps protect businesses from cyberattacks, data breaches, and other malicious activities. Security is also important for protecting the privacy of customers, employees, and other stakeholders. Security helps ensure that confidential information is kept secure and that only authorized individuals can access it. Security also helps protect companies from financial losses due to data breaches and other cyberattacks.
Goals Of Data Security
The three goals of data security are confidentiality, integrity, and availability. Confidentiality is the protection of data from unauthorized access, while integrity is the assurance that data has not been modified or changed in any way. Availability is the assurance that data is accessible and usable when needed. These goals are important for protecting data and ensuring that it is used appropriately.
Why Security Is More Important Than Privacy?
Security is more important than privacy because it helps to protect data and systems from unauthorized access, modification, or destruction. Security measures help to ensure that data is kept confidential, integrity is maintained, and availability is guaranteed. Security is also important for preventing malicious attacks and protecting against data breaches. Privacy, on the other hand, is more focused on protecting individuals from having their personal information shared or used without their consent.
Elements Of Data Security
1. Authentication: Authentication is the process of verifying the identity of a user or system. This is usually done through the use of passwords, biometrics, or other forms of identification.
2. Access Control: Access control is the process of granting or denying access to certain resources based on a user’s identity. This is usually done through the use of role-based access control.
3. Encryption: Encryption is the process of encoding data so that it can only be accessed by authorized users. This is done to protect sensitive data from unauthorized access.
4. Data Backup: Data backup is the process of creating copies of data in order to protect against data loss in the event of a disaster or system failure.
Levels Of Data Security
1. Physical security: Physical security involves measures taken to protect data from physical damage or theft. This includes measures such as locks, surveillance, and access control.
2. Network security: Network security involves measures taken to protect data from unauthorized access over a network. This includes measures such as firewalls, encryption, and authentication.
3. Application security: Application security involves measures taken to protect data from malicious software and unauthorized access. This includes measures such as antivirus software, application firewalls, and user authentication.
What Is Data Security Called?
Data security is a term used to describe the measures taken to protect data from unauthorized access, use, disclosure, disruption, modification, or destruction. It involves measures such as encryption, authentication, and access control.
Improve Data Security
To improve data security, organizations should implement a comprehensive data security strategy that includes the following measures:
1. Implement strong authentication and access control measures.
2. Use encryption to protect data in transit and at rest.
3. Monitor systems for suspicious activity and respond quickly to any threats.
4. Regularly patch systems and applications to reduce vulnerabilities.
5. Educate users about data security and enforce policies.
6. Utilize data loss prevention technologies.
NewSoftwares Inc. is a Beaverton, U.S based company that provides data and information protection and online backup solutions to its global client base.
