Introduction
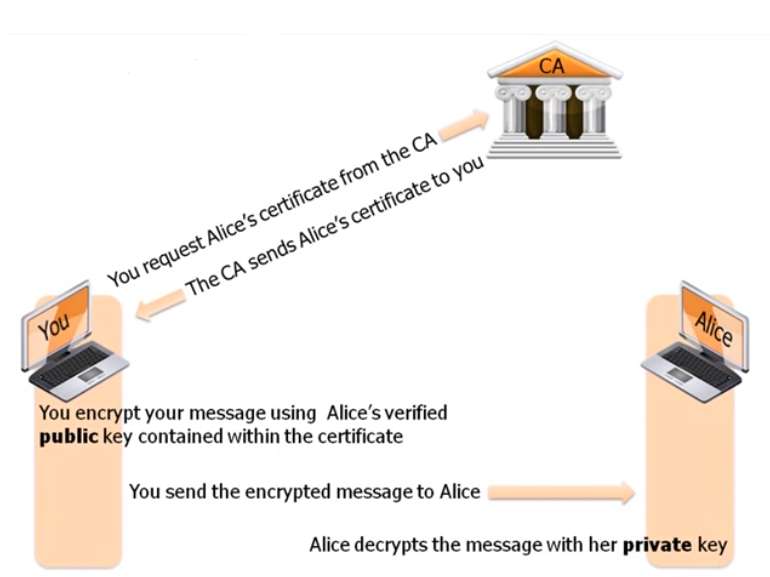
Public Key Infrastructure (PKI) encryption is a method of encrypting data that relies on a pair of keys – a public key and a private key. The public key is used to encrypt data, while the private key is used to decrypt the data. This type of encryption is widely used in secure communication over the Internet, such as online banking, e-commerce, and email encryption. Exploring the Intricacies of PKI Encryption: Which Key Encrypts the Data?
PKI encryption involves a complex process of generating a public and private key pair, which are mathematically related but cannot be derived from each other. The public key is shared with anyone who needs to send encrypted data, while the private key is kept secret and only known to the owner. When a sender wants to send encrypted data to a receiver, they use the receiver’s public key to encrypt the data. Once the data is encrypted, only the receiver with the corresponding private key can decrypt and read the message.
Focus On The Primary Question: Which Key Encrypts The Data In The PKI Encryption Method?
In PKI encryption, the data is encrypted using the recipient’s public key. The recipient’s private key is used to decrypt the data.
The Role Of Public And Private Keys In PKI Encryption
Public and private keys are fundamental components of PKI encryption. Public keys are used to encrypt data, while private keys are used to decrypt it. The public key is widely distributed and can be accessed by anyone, while the private key is kept secret and only accessible to the owner. When a sender wants to send a message to a receiver, they use the receiver’s public key to encrypt the message. The receiver then uses their private key to decrypt the message. This process ensures that only the intended recipient can read the message, as only they have the private key necessary to decrypt it.
Similarly, when a sender wants to digitally sign a message, they use their private key to create a unique digital signature. The receiver can then verify the signature using the sender’s public key, ensuring that the message was not tampered with and that the sender is who they claim to be.
How Public And Private Keys Work Together In PKI Encryption?
Public key infrastructure (PKI) encryption relies on the use of both public and private keys to ensure secure communication. Public keys are widely distributed and can be freely shared. They are used to encrypt messages and data before they are sent over a network. When a message is encrypted with a public key, only the corresponding private key can decrypt it. This ensures that only the intended recipient can read the message.
Private keys, on the other hand, are kept secret and are only known to the owner of the key pair. Private keys are used to decrypt messages that have been encrypted with the corresponding public key. Additionally, private keys are used to digitally sign messages, which provides a way to verify the authenticity of the sender.
When a sender wants to send a message to a receiver using PKI encryption, they first encrypt the message using the receiver’s public key. The receiver can then decrypt the message using their private key. If the sender wants to digitally sign the message, they use their private key to create a unique digital signature. The receiver can then verify the signature using the sender’s public key, ensuring that the message was not tampered with and that the sender is who they claim to be.
Differences Between Public And Private Keys
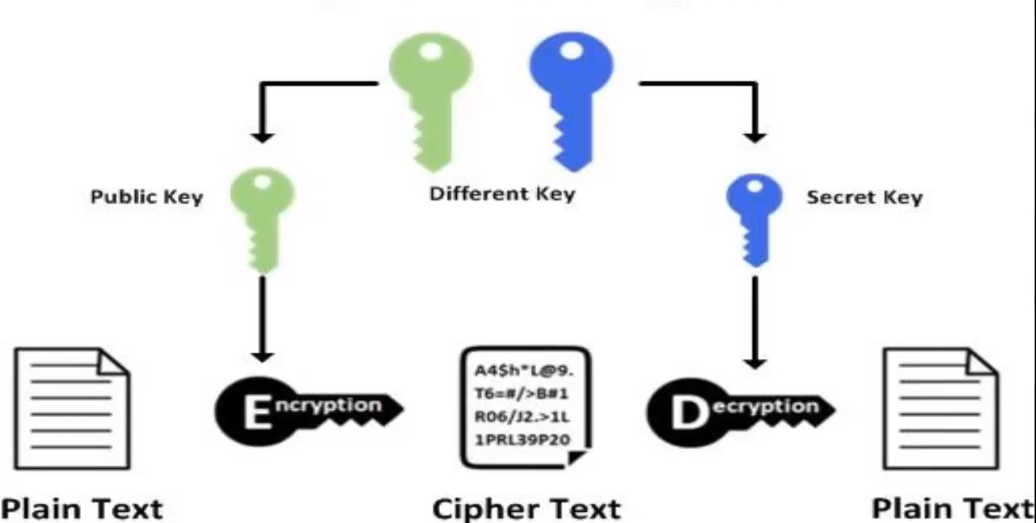
Public and private keys are both used in cryptography to secure communication and authenticate users, but they have some key differences.
Firstly, the public key is freely available to anyone, while the private key is kept secret and only known to the owner.
Secondly, the public key is used to encrypt messages, while the private key is used to decrypt them.
Thirdly, the public key can be used to verify digital signatures, while the private key is used to create them.
Finally, public keys are often used for key exchange in secure communication protocols, while private keys are used for authentication and access control. It’s important to keep the private key secure and not share it with anyone, as it is the key to decrypting messages and accessing sensitive information. Public keys, on the other hand, can be shared freely and are often used for secure communication with unknown parties, as they allow for secure encryption without the need for a shared secret key.
How Public And Private Keys Are Generated?
Public and private keys are generated using complex mathematical algorithms known as cryptographic key pairs. These algorithms generate two mathematically related keys – a public key and a private key – that are unique to each user. The private key is kept secret and known only to the owner, while the public key can be shared with anyone. To generate a key pair, the user typically uses a software program or service that implements the cryptographic algorithm. The program generates a random number, which is used as the private key, and then uses the private key to generate the corresponding public key. The public key can then be shared with others, allowing them to encrypt messages or data that can only be decrypted by the owner of the private key. This process of generating and using key pairs is essential for secure communication over the internet, as it allows users to encrypt and decrypt messages without the risk of interception or tampering by third parties. It is used in a variety of applications, including email encryption, online banking, and secure messaging.
What Is The Purpose Of Having The Server Encrypt Data Using Its Private Key?
The purpose of having the server encrypt data using its private key is to provide a secure and authenticated communication channel between the server and the client. When the server encrypts data using its private key, only the client with the corresponding public key can decrypt and access the data. This ensures that the data is not tampered with or intercepted by any third party during transmission. Additionally, the use of private key encryption also ensures that the communication is authenticated, meaning that the client can be sure that the data is coming from the server and not from an impostor.
How Data Is Encrypted Using Public Key?
When data is encrypted using a public key, the sender first obtains the recipient’s public key. The sender then uses this public key to encrypt the data before sending it to the recipient. The public key is used to encrypt the data because it is available to anyone who wants to send a message to the recipient. Once the data is encrypted, only the recipient can decrypt it using their private key. This is because the private key is kept secret by the recipient who is required to decrypt the data. This ensures that only the intended recipient can access the data and that it remains secure from unauthorized access or interception during transmission.
Overall, the use of public and private keys in PKI provides a secure and reliable method for encrypting and decrypting data, ensuring that sensitive information remains confidential and protected.
How Data Is Decrypted Using The Private Key?
When data is encrypted using a public key, it can only be decrypted using the corresponding private key. The recipient of the encrypted data uses their private key to decrypt it, which involves reversing the encryption process. The private key is used to perform a mathematical calculation that reverses the transformation of the data carried out by the public key. Once the data has been decrypted, it can be accessed and read by the recipient. It’s important to note that the private key must be kept secure and confidential to prevent unauthorized decryption of the data.
Why The Private Key Cannot Be Used To Encrypt Data
The private key cannot be used to encrypt data because it is designed to be kept secret and known only to the owner of the key. If the private key were used to encrypt data, anyone with access to the public key could easily decrypt it, which would compromise the security of the communication system. Instead, the public key is used for encryption, and the private key is used for decryption. This way, only the intended recipient, who has the corresponding private key, can decrypt the message and access the encrypted data. This is the basic principle of public-key cryptography, which is widely used for secure communication over the Internet. In this system, each user has a pair of keys, a public key and a private key, which are mathematically related but cannot be derived from each other. The public key is shared with others, while the private key is kept secret.
Discussion On Why The Public Key Is Used For Data Encryption In PKI
The public key is used for data encryption in PKI because it allows for secure communication between two parties without the need for them to exchange a secret key beforehand. This is because the public key can be freely shared with anyone, while the private key remains secret and only known to the owner. When a sender wants to send a message to a recipient, they encrypt the message using the recipient’s public key. This ensures that only the recipient, who possesses the corresponding private key, can decrypt and read the message.
Using the public key for encryption also provides an added layer of security, as it means that even if the public key is intercepted by an attacker, they will not be able to decrypt the message without the private key.
Conclusion
Understanding which key encrypts data in PKI encryption is crucial for ensuring the security and integrity of online transactions. It is important to recognize the differences between public and private keys and how they are used in the encryption process. By implementing PKI encryption and properly managing keys, organizations can safeguard their sensitive data and maintain the trust of their stakeholders. As the digital landscape continues to evolve, it is essential to stay informed and vigilant in protecting against cyber threats.
Frequently Asked Questions (FAQs)
How Secure Is PKI Encryption?
PKI encryption is considered to be highly secure due to its use of public and private keys. The public key is used to encrypt the data, while the private key is used to decrypt it. As the private key is kept secret and only accessible to the intended recipient, it’s very difficult for unauthorized parties to access the encrypted data. Additionally, PKI encryption uses digital certificates to verify the identity of the sender and recipient, further enhancing its security.
How Is PKI Encryption Different From Other Encryption Methods?
PKI encryption is different from other encryption methods in several ways. Firstly, it uses a public and private key pair to encrypt and decrypt data, which makes it more secure than symmetric key encryption. Secondly, it uses a digital certificate to verify the identity of the sender and receiver of the data, which provides an additional layer of security. Finally, PKI encryption can be scaled to meet the needs of organizations of all sizes and can be a cost-effective solution for data security in the long run.
How Is PKI Encryption Used In Digital Signatures?
PKI encryption is an essential component of digital signatures. When someone signs a document digitally, they use their private key to encrypt a hash of the document. This encrypted hash is then sent along with the document to the recipient. The recipient can then use the sender’s public key, which is stored in a digital certificate, to decrypt the encrypted hash. If the decrypted hash matches the hash of the received document, it proves that the document has not been tampered with and that it was indeed sent by the sender who possesses the private key. This process ensures the authenticity and integrity of the document, making digital signatures a reliable and secure way to sign documents electronically.
How Do Public And Private Keys Enhance Security In PKI Encryption?
Public and private keys enhance security in PKI encryption by providing a secure way to encrypt and decrypt data. In PKI, the public key is used to encrypt data, while the private key is used to decrypt it. Since the private key is kept secret by the owner, only the owner can decrypt the data, ensuring that the data remains secure. Furthermore, digital certificates, which contain the public key, are issued by trusted third-party entities called Certificate Authorities (CAs). The use of CAs in PKI helps to establish trust between parties by verifying the authenticity of the public key and the identity of the certificate holder. This helps to prevent man-in-the-middle attacks and other forms of cyber threats. Overall, PKI encryption provides a highly secure way to transmit sensitive data over the internet and is widely used in industries such as finance, healthcare, and government. By using public and private keys, and digital certificates issued by trusted CAs, PKI encryption helps to ensure the confidentiality, integrity, and authenticity of data, making it a crucial component of modern cybersecurity. In addition to its security benefits, PKI encryption also offers several practical advantages. For example, it enables secure remote access to networks and systems, allowing employees to work from home or on the go without compromising the security of sensitive data. It also facilitates secure e-commerce transactions, allowing customers to make purchases online with the confidence that their personal and financial information is protected.
Overall, PKI encryption is a powerful tool for securing sensitive data and ensuring the integrity of online transactions. Its use is becoming increasingly important as more and more business is conducted online, and as the threat of cyber attacks continues to grow. By implementing PKI encryption, organizations can protect their valuable data and maintain the trust of their customers and partners.
