Introduction
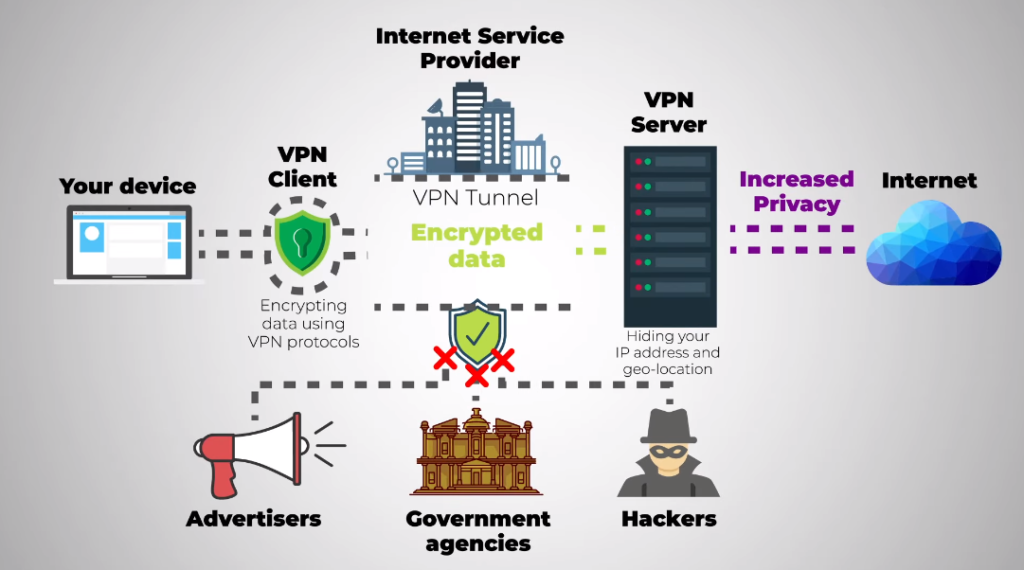
A virtual private network (VPN) permits users to establish a secure and encrypted connection between their device and a remote server. This is achieved through the use of various VPN protocols, each with its own set of features and security measures. This article will explore the VPN protocols to establish a secure connection and encrypt data.
Importance Of VPN Protocols In Establishing A Secure Connection And Encrypting Data
VPN protocols are crucial in establishing a secure connection and encrypting data during transmission. They confirm that data is protected from unauthorized access and interception by encrypting it before transmitting it over the internet. By using VPN protocols like L2TP and SSTP, users can establish a secure tunnel between their device and the VPN server, which ensures that all data transmitted between the two devices is encrypted and secure.L2TP provides a high level of security by using encryption to protect data during transmission. It is widely used for VPN connections and is supported by many operating systems. SSTP, on the other hand, uses SSL/TLS encryption to establish a secure connection between two devices. It provides strong security and is resistant to attacks such as man-in-the-middle attacks.
VPN Protocols: Establishing Secure Connections
There are several VPN protocols that are designed to establish a secure connection and encrypt data. These include:
- OpenVPN: This is an open-source VPN protocol that is known for its flexibility and security. It uses SSL/TLS for exchanges of key and can work on any port, making it reliable and difficult to block.
- IKEv2/IPsec: Internet Key Exchange version 2 (IKEv2) is a VPN protocol that is quick and efficient. It is paired with IPsec for encryption and security. This protocol is particularly effective at reestablishing a VPN connection when internet connectivity is interrupted.
- L2TP/IPsec: Layer 2 Tunneling Protocol (L2TP) is often used together with IPsec to provide a secure VPN connection. It does not offer encryption itself, but IPsec provides the security and encryption measures.
- SSTP: Secure Socket Tunneling Protocol (SSTP) is owned by Microsoft and provides a secure VPN connection, as it uses SSL/TLS for key exchange.
- WireGuard: This is a newer VPN protocol known for its speed, performance, and simplicity. It uses state-of-the-art cryptography to provide a secure connection.
- PPTP: Point-to-Point Tunneling Protocol (PPTP) is one of the oldest VPN protocols. Although it is widely supported, it is also known to have significant security vulnerabilities.
Remember, while all of these protocols provide a secure connection and encrypt data, their effectiveness may vary based on the specific use case, hardware, network conditions, and security needs. It is essential to use a trusted VPN service and ensure your protocol of choice aligns with your security requirements.
OpenVPN Protocol
Advantages And Disadvantages Of OpenVPN Protocol
OpenVPN is a popular open-source VPN protocol with strong encryption and authentication capabilities.
Some advantages of using OpenVPN include:
1. Strong security: OpenVPN uses SSL/TLS encryption to secure the communication between the client and the server, providing strong protection against eavesdropping and other attacks.
2. Flexibility: OpenVPN can be used with several operating systems and devices, like Windows, macOS, Linux, Android, and iOS.
3. Customizability: OpenVPN is highly customizable, allowing users to configure various settings such as encryption algorithms, authentication methods, and network topology.
There are also some disadvantages to using OpenVPN:
1. Performance: OpenVPN can be slower than other VPN protocols, especially when using high levels of encryption.
2. Complexity: OpenVPN can be more complex to set up and configure than other VPN protocols, requiring some technical expertise.
3. Compatibility: Some firewalls and network configurations may not be compatible with OpenVPN, making it difficult to establish a connection.
Security Features Of OpenVPN Protocol
OpenVPN is known for its high-security features, making it the best choice for users who prioritize privacy and security. Some of the key security features of OpenVPN include:
1. Strong encryption: OpenVPN uses 256-bit encryption, considered one of the strongest. This ensures that any data transmitted through the VPN is protected from prying eyes.
2. Authentication: OpenVPN uses digital certificates and pre-shared keys to authenticate users and ensure that only authorized users can access the VPN.
3. Perfect forward secrecy: OpenVPN uses Perfect Forward Secrecy (PFS), which ensures that even if an attacker can compromise the encryption key, they cannot decrypt past or future communication.
4. Firewall and NAT traversal: OpenVPN is designed to work with firewalls and Network Address Translation (NAT) devices, making it easier to set up and use in various network environments.
Strong encryption, authentication, and other security features make OpenVPN a highly secure VPN protocol.
PPTP Protocol
Advantages And Disadvantages Of The PPTP Protocol
Advantages
- Most operating systems and devices widely support PPTP.
- It is comparatively easy to set up and configure, making it a popular choice for beginners.
- PPTP is generally faster than other VPN protocols due to its low encryption overhead.
Disadvantages
- PPTP is less secure than other VPN protocols, as it uses weaker encryption methods.
- It is vulnerable to certain types of attacks, such as brute force attacks, which can compromise the security of your data.
- PPTP is not recommended in countries with strict censorship laws, as ISPs can easily block it.
Security Concerns With The PPTP Protocol
The PPTP (Point-to-Point Tunneling Protocol) protocol has several security concerns that make it less secure than other VPN protocols. One of the main issues with PPTP is that it uses weak encryption, which makes it vulnerable to certain types of attacks, such as brute force attacks. This can compromise the security of your data and leave you vulnerable to hackers and other malicious actors. Another concern with PPTP is that it does not authenticate the transmitted data, making it susceptible to man-in-the-middle attacks. This can allow an attacker to intercept and modify your data, potentially exposing sensitive information.
Finally, PPTP is not recommended in countries with strict censorship laws, as ISPs can easily block it. This can limit your ability to access certain websites and services and make it more difficult to use the VPN service.
L2TP Protocol
Advantages And Disadvantages Of L2TP Protocol
The L2TP (Layer 2 Tunneling Protocol) is a popular VPN protocol offering security and speed. Some advantages of using L2TP include its compatibility with various devices and operating systems and its ability to provide strong encryption for data transmission. However, one disadvantage of L2TP is that it can be slower than other VPN protocols, such as OpenVPN. L2TP does not provide built-in authentication, which must be combined with another protocol, such as IPSec, to ensure secure data transmission.
Security Concerns With The L2TP Protocol
L2TP protocol has been criticized for its security vulnerabilities, particularly in encryption. L2TP only provides encryption for the data payload and not for the header information, which can potentially be intercepted and used to identify the source and destination of the communication. Additionally, L2TP relies on pre-shared keys for authentication, which can be vulnerable to brute-force attacks or other forms of hacking. It is recommended that L2TP be combined with IPSec for improved security.
IKEv2 Protocol
Advantages And Disadvantages Of The IKEv2 Protocol
IKEv2 (Internet Key Exchange version 2) is another popular VPN protocol with strong security features.
Some advantages of using IKEv2 include:
- Speed and stability: IKEv2 is known for its fast connection speed and reliable performance.
- Mobile compatibility: IKEv2 is often used for mobile devices, as it has been designed to handle network changes and interruptions seamlessly.
- Strong security: Like OpenVPN, IKEv2 uses strong encryption and authentication protocols to protect your data.
However, there are also some disadvantages to using IKEv2:
- Limited support: While most modern operating systems support IKEv2, it may not be as widely supported as other VPN protocols.
- Configuration complexity: Setting up IKEv2 can be more complex than other VPN protocols, which may make it less accessible to some users.
Security Features Of The IKEv2 Protocol
IKEv2 protocol provides strong security features, making it a popular choice among users who prioritize privacy and security. Here are some of the key security features of IKEv2:
- Encryption: IKEv2 uses strong encryption algorithms such as AES and SHA-2 to secure data transmissions between the VPN client and server.
- Authentication: IKEv2 supports multiple authentication methods, including digital certificates, pre-shared keys, and username/password combinations, to ensure that only sanctioned users can access the VPN.
- Perfect forward secrecy: IKEv2 uses perfect forward secrecy (PFS) to generate a unique encryption key for each session, making it more difficult for hackers to decrypt past sessions even if they gain access to the encryption keys.
4. Tunneling: IKEv2 supports user datagram protocol (UDP) and transmission control protocol (TCP) tunneling, allowing it to bypass firewalls and other network restrictions.
SSTP Protocol
Advantages And Disadvantages Of The SSTP Protocol
Here are the advantages and disadvantages of the SSTP protocol:
Advantages:
1. Secure: SSTP uses SSL/TLS encryption, which is highly secure and difficult to crack.
2. Firewall-friendly: SSTP uses the same port as HTTPS (port 443), which is usually open on most firewalls, making it easy to use in restricted environments.
3. Cross-platform compatibility: SSTP is supported on Windows, Linux, and macOS, making it a viable option for users on different operating systems.
4. Stable: SSTP is known for its stability and reliable performance.
Disadvantages:
1. Limited support: SSTP is primarily supported by Microsoft platforms, which limits its availability on other platforms.
2. Closed source: SSTP is a proprietary protocol developed by Microsoft, which means its code is not open for independent review.
3. Potential for NSA involvement: There have been concerns that the NSA may have influenced the development of SSTP, which raises questions about its security.
4. Slower speeds: SSTP can be slower than other VPN protocols due to SSL/TLS encryption overhead.
Security Features Of The SSTP Protocol
SSTP protocol offers several security features, including:
1. SSL/TLS encryption: SSTP uses SSL/TLS encryption to secure the data transmitted between the client and server.
2. Authentication: SSTP supports various authentication methods, including EAP, MS-CHAP, and MS-CHAP v2.
3. Firewall traversal: SSTP can traverse firewalls and network address translation (NAT) devices without additional configuration.
4. Integrity checking: SSTP uses SHA-1 or SHA-256 to ensure the integrity of the data transmitted over the VPN connection.
5. Certificate-based authentication: SSTP can use digital certificates to provide an additional security layer.
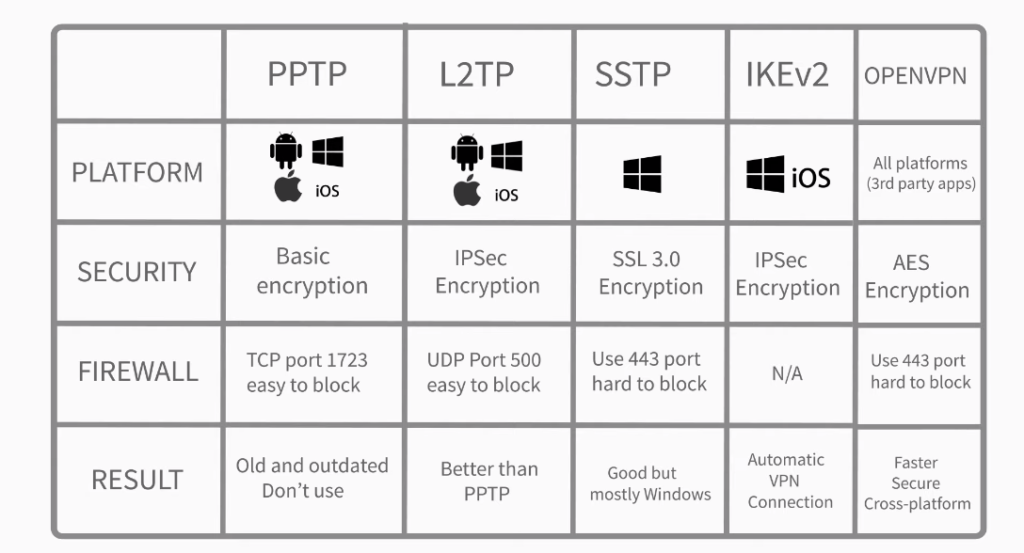
Comparison Of VPN Protocols
When comparing VPN protocols, it’s important to consider security, speed, and compatibility with different devices and operating systems. Here’s a brief comparison of some popular VPN protocols:
1. OpenVPN: This open-source protocol is considered one of the most secure VPN options. It can be used with various encryption algorithms and is compatible with most operating systems.
2. IPSec: This protocol is commonly used for site-to-site VPN connections and is known for its strong security features. It can be used with multiple encryption algorithms and is supported by most operating systems.
3. L2TP/IPSec: This protocol combines the security of IPSec with the speed of L2TP. Most operating systems widely support it, but it may not be the best option for users in countries with strict censorship laws.
4. PPTP: This protocol is one of the oldest and most widely used VPN options. It’s fast and easy to set up but is considered less secure than other options due to vulnerabilities in its encryption.
5. SSTP: As mentioned earlier, SSTP is a Microsoft-developed protocol that provides strong encryption and authentication mechanisms. However, its closed-source nature and potential NSA involvement may raise some concerns about its security.
Choosing The Best VPN Protocol For My Needs
Choosing the best VPN protocol for your needs depends on several factors, such as your device, security requirements, and online activities. Here are some tips to help you select the right VPN protocol:
1. Consider your device: Some VPN protocols are incompatible with all devices. For example, PPTP is an older protocol that may not work with newer devices. Check the compatibility of the protocol with your device before choosing it.
2. Determine your security requirements: Different VPN protocols offer varying levels of security. For example, OpenVPN is considered the most secure protocol, while PPTP is the least secure. Consider your security needs when choosing a protocol.
3. Evaluate your online activities: Some VPN protocols may better suit certain online activities. For example, if you plan on streaming video content, you may want to choose a protocol that offers faster connection speeds.
4. Test different protocols: Many VPN services offer multiple protocols, so it’s good to test different ones to see which performs best. Try switching between protocols to see which offers your needs the best performance and security.
Conclusion
This article covered several VPN protocols, including PPTP, L2TP/IPSec, OpenVPN, IKEv2, and SSTP. Each protocol has strengths and weaknesses, and choosing the right one for your needs is important. Factors to consider when choosing a protocol include security, speed, and compatibility with your devices and online activities. It’s also a good idea to test different protocols to see which offers the best performance and security for your needs.
Frequently Asked Questions (FAQs)
What Is A VPN?
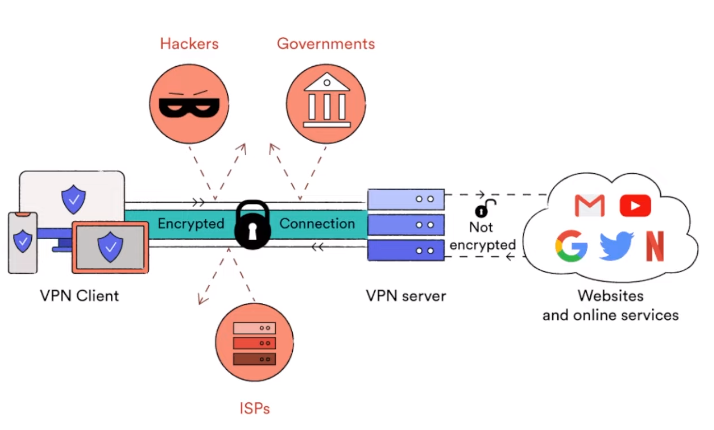
A Virtual Private Network is a technology that permits you to create a secure and private connection to the internet. It does this by directing your internet traffic via a remote server and encrypting it, making it problematic for anyone to interrupt or spy on your online activities. VPNs are commonly applied to protect online privacy, bypass internet censorship, and access geo-restricted content.
Which VPN Protocol Is The Most Secure?
A VPN protocol is a set of rules and measures that govern how data is transmitted between devices in a VPN network. Several VPN protocols are available, including OpenVPN, L2TP/IPSec, PPTP, and SSTP. In terms of security, OpenVPN is generally considered the most secure VPN protocol. It uses strong encryption and supports many cryptographic algorithms, making it difficult for hackers to break into.
Can I Use Multiple VPN Protocols At Once?
No, it is not possible to use multiple VPN protocols at once. A VPN connection can only use one protocol at a time. However, some VPN providers may offer multiple protocol options for users, allowing them to select the most appropriate protocol for their needs. It’s important to note that using multiple VPNs simultaneously can decrease security and cause connectivity issues.
Do All VPN Services Offer Multiple Protocols?
Not all VPN services offer multiple protocols, but many do. It’s important to research and compares different VPN providers to determine which offer features and protocols best suit your needs. Some common VPN protocols include OpenVPN, PPTP, L2TP, and IKEv2. When choosing a VPN service, it’s important to consider factors such as encryption strength, server locations, and connection speeds.
