Introduction
In today’s digital landscape, data security is of paramount importance. With the constant threats of cyber-attacks and data breaches, organizations and individuals are increasingly relying on encryption to protect sensitive information. Encryption is the process of converting data into a format that is unreadable to unauthorized users. When it comes to servers, various methods and technologies are employed to encrypt data and ensure its confidentiality and integrity. This article explores the different tools and techniques used to encrypt data on a server.
Importance of Data Encryption
Data encryption plays a crucial role in safeguarding information stored on servers. It provides an additional layer of protection, making it difficult for unauthorized individuals to access or interpret sensitive data. By encrypting data, even if it is intercepted or stolen, it remains unreadable and unusable without the appropriate decryption key. This significantly reduces the risk of data breaches and helps maintain the privacy and trust of users.
Encryption Methods
There are several encryption methods used to secure data on servers. These methods employ various cryptographic algorithms and protocols to convert plain text into ciphertext. Let’s explore some of the commonly used encryption techniques.
Secure Sockets Layer (SSL)
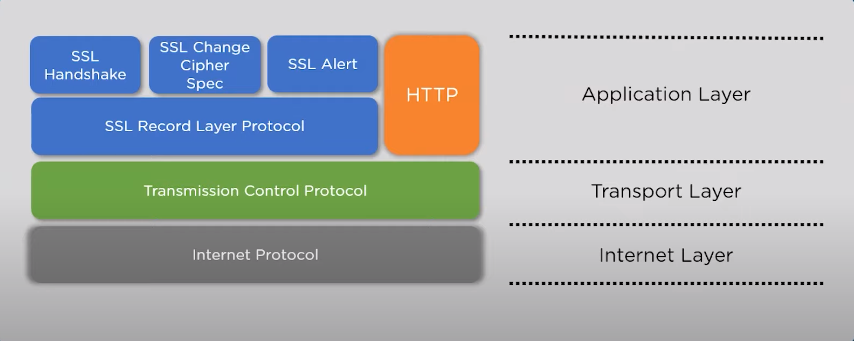
SSL is a widely used encryption protocol that establishes an encrypted link between a client and a server. It ensures secure communication by encrypting data transmitted between web browsers and web servers. SSL certificates validate the identity of the server and enable secure data transfer, protecting sensitive information such as login credentials, credit card details, and personal data.
Transport Layer Security (TLS)
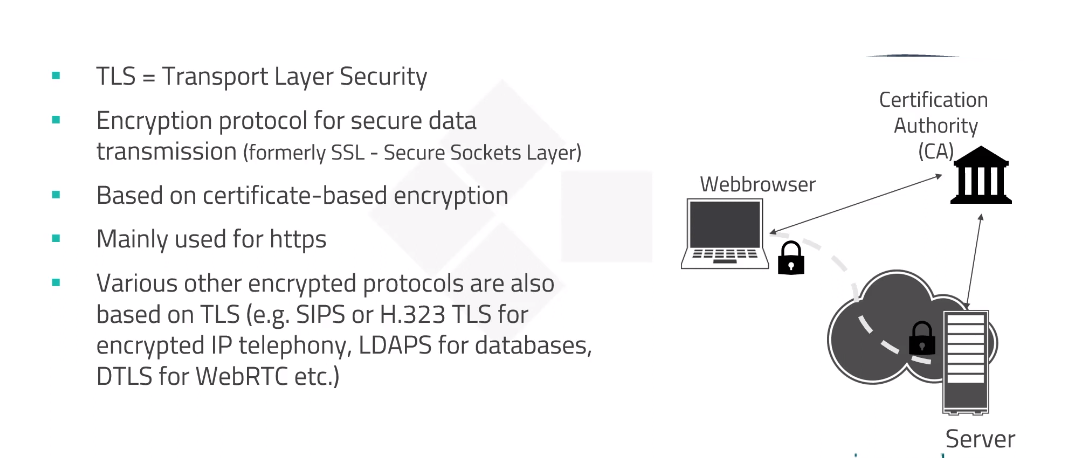
TLS is an upgraded version of SSL and is widely used to secure internet communications. It provides encryption and authentication services, ensuring the privacy and integrity of data transmitted between clients and servers. TLS is essential for secure email communication, online banking, e-commerce transactions, and other sensitive online activities.
Secure File Transfer Protocol (SFTP)

SFTP is a secure extension of the File Transfer Protocol (FTP) that adds encryption and authentication capabilities. It enables secure file transfers between a client and a server, protecting the confidentiality of data during transmission. SFTP is commonly used for transferring sensitive files, ensuring they remain protected from unauthorized access.
Secure Shell (SSH)
SSH is a cryptographic network protocol that provides secure remote access to servers. It establishes an encrypted connection between a client and a server, preventing eavesdropping and unauthorized access. SSH encrypts the session and provides secure authentication, making it a popular choice for remote administration and secure file transfers.
Virtual Private Networks (VPNs)
VPNs create a secure and encrypted connection between a user’s device and a server through a private network. By routing the internet traffic through an encrypted tunnel, VPNs ensure data confidentiality and protect against eavesdropping. VPNs are commonly used to establish secure connections in remote work environments and for accessing geographically restricted content.
Full Disk Encryption
Full Disk Encryption (FDE) is a technique that encrypts an entire disk or storage device. It ensures that all data stored on the disk remains encrypted, even if the device is lost or stolen. FDE protects against unauthorized access by requiring a decryption key or passphrase during system boot-up or disk access.
Database Encryption
Database encryption involves encrypting sensitive data stored within a database system. It protects data at rest and in transit, preventing unauthorized access to the database files. Database encryption can be implemented at the file level, column level, or even individual cell level, depending on the level of granularity required.
Encryption Key Management
Encryption keys are an integral part of the encryption process. They are used to encrypt and decrypt data, and their security is crucial for maintaining the confidentiality of encrypted information. Proper encryption key management involves generating strong keys, securely storing and transmitting them, and ensuring their timely rotation to minimize the risk of key compromise.
Encryption Algorithms
Encryption algorithms are mathematical functions used to transform plaintext into ciphertext and vice versa. There are various encryption algorithms available, each with its own strengths and weaknesses. Commonly used encryption algorithms include Advanced Encryption Standard (AES), Rivest Cipher (RC), and Data Encryption Standard (DES).
Benefits of Data Encryption
Data encryption offers numerous benefits for server security:
- Confidentiality: Encryption ensures that only authorized individuals can access sensitive data, maintaining its confidentiality.
- Integrity: Encryption protects data from unauthorized modifications, ensuring its integrity and authenticity.
- Compliance: Many industry regulations and data protection laws require the use of encryption to protect sensitive information.
- Trust and Reputation: Implementing strong data encryption measures helps build trust with customers and stakeholders, enhancing an organization’s reputation.
Limitations of Data Encryption
While data encryption is highly effective in protecting data, it does have some limitations:
- Key Management: Proper key management is essential for effective encryption. If encryption keys are lost or compromised, the encrypted data may become permanently inaccessible.
- Performance Impact: Encryption and decryption processes can introduce additional computational overhead, which may impact server performance, especially for high-traffic websites or resource-intensive applications.
- Data Recovery: If encryption keys are lost, recovering encrypted data can be extremely challenging or impossible.
FAQs
What is the purpose of data encryption?
Data encryption is used to convert sensitive information into an unreadable format to protect it from unauthorized access and maintain its confidentiality.
What are some commonly used encryption methods?
Commonly used encryption methods include SSL, TLS, SFTP, SSH, VPNs, full disk encryption, and database encryption.
How do encryption algorithms work?
Encryption algorithms use mathematical functions to transform plaintext into ciphertext. The process involves applying a specific algorithm and an encryption key to convert the data.
What is the role of encryption key management?
Encryption key management involves generating, storing, and securely managing encryption keys to ensure the confidentiality and integrity of encrypted data.
What are the limitations of data encryption?
Data encryption can have limitations in terms of key management, performance impact, and data recovery if encryption keys are lost or compromised. However, these limitations can be mitigated with proper implementation and management practices.
Conclusion
In an era where data security is paramount, encrypting data on servers is crucial to protect sensitive information from unauthorized access. Various encryption methods, such as SSL, TLS, SFTP, SSH, VPNs, FDE, and database encryption, provide robust security measures to safeguard data at rest and in transit. Encryption algorithms and key management play vital roles in ensuring the confidentiality and integrity of encrypted data. By implementing strong encryption practices, organizations can mitigate the risk of data breaches, build trust with their users, and comply with data protection regulations.
