Phishing is a deceptive cybercrime where attackers impersonate trusted sources to steal personal information. To avoid falling victim to phishing, recognize red flags like unsolicited emails, urgent language, and mismatched URLs. Always verify the sender’s identity and use strong, unique passwords with two-factor authentication. Keep software updated, be cautious with links and downloads, and educate yourself about phishing techniques. Installing reliable antivirus software adds an extra layer of protection.
What is Phishing?

Phishing is a form of cybercrime where attackers masquerade as trustworthy entities, often through emails, websites, or messages, with the aim of stealing sensitive information. This can include personal data, financial details, login credentials, and more. The term “phishing” is derived from “fishing,” as cybercriminals cast a wide net, hoping to lure unsuspecting victims.
How Phishing Works?
1. Bait Creation:
Phishers begin by creating an enticing lure, often in the form of an email, but it can also be a message, a website, or a phone call. This bait is designed to appear legitimate and trustworthy. It typically mimics a reputable organization or individual with whom the target would likely interact daily. Common examples include emails pretending to be from banks, social media platforms, government agencies, or popular online services.
2. Hooking the Victim:
Once the bait is set, the attacker aims to hook the victim. This is where the recipient of the phishing attempt comes into play. The victim receives the deceptive communication and is urged to take specific actions. These actions could include:
- Clicking on a Link: The email may contain a link that directs the victim to a fraudulent website. This website is designed to look like a legitimate organization’s site, complete with logos, branding, and convincing forms.
- Downloading Malware: In some cases, clicking on a link or downloading an attachment can result in the installation of malware on the victim’s device. This malware can steal information, track the victim’s activities, or enable further attacks.
- Providing Information: Phishing emails often request sensitive information, such as login credentials, credit card numbers, Social Security numbers, or other personal details. Victims may be tricked into filling out forms or responding to seemingly urgent requests.
3. Data Harvesting:
Once the victim takes the prescribed action, the attacker harvests the information they seek. This can include:
- Login Credentials: If the victim enters their username and password on a fake website, the phisher gains access to their accounts.
- Financial Information: Credit card numbers or bank account details can be stolen if victims provide them in response to a phishing email.
- Personal Identifying Information (PII): Phishers may seek PII, such as Social Security numbers or birthdates, which can be used for identity theft.
4. Covering Tracks:
After obtaining the desired information, the attacker may attempt to cover their tracks. This can involve deleting any traces of their activities or maintaining a deceptive presence to continue extracting data over time.
5. Exit Strategy:
Once the attacker has achieved their goals, they may either disappear or continue to use the stolen information for further illicit activities. This could include financial fraud, identity theft, or selling the data on the dark web.
Recognizing Phishing Attempts:
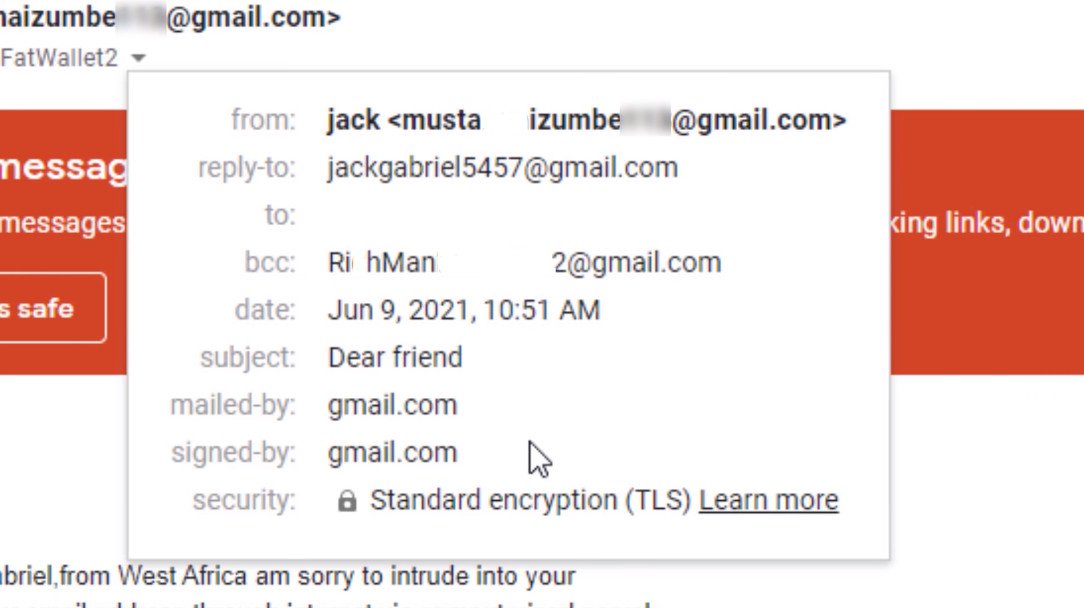
1. Check the Sender’s Email Address
- Suspicious or Misspelled Email Addresses: Scrutinize the sender’s email address. Phishers often use email addresses that are slightly altered or misspelled to mimic legitimate sources. For example, “support@yourbank.com” might become “support@yourbank1.com.”
2. Examine the Email Content
- Urgent or Threatening Language: Phishing emails often create a sense of urgency or use threatening language to pressure recipients into taking immediate action. They may claim that your account will be suspended, or you’ll face legal consequences if you don’t act right away.
- Generic Greetings: Phishing emails may use generic greetings like “Dear Customer” instead of addressing you by your name.
- Misspelled Words and Grammar Errors: Phishing emails often contain typos, grammatical mistakes, or awkward language that can indicate a lack of professionalism.
- Unexpected Attachments or Links: Be cautious of unexpected attachments or links, especially if you weren’t expecting them. Hover your mouse over links to see the actual URL before clicking.
- Unsolicited Requests for Personal Information: Legitimate organizations usually don’t request sensitive information via email. Be skeptical of emails asking for passwords, Social Security numbers, credit card details, or other personal data.
3. Verify the Email’s Authenticity
- Contact the Organization Directly: If you receive an email requesting sensitive information or actions, independently verify its legitimacy. Don’t use the contact information provided in the email itself; instead, visit the official website or use the contact information you already have.
- Search for Official Communication: If you receive an email from a bank, service provider, or government agency that seems suspicious, search online for recent official announcements or communications from that entity. Compare the email you received with known legitimate sources.
- Check for HTTPS: When visiting websites, ensure they use the “https://” protocol and have a padlock symbol in the address bar. This indicates a secure connection.
4. Be Cautious with Pop-Up Windows
- Close Pop-Ups: If you encounter pop-up windows while browsing that ask for personal information or login credentials, close them. Legitimate websites typically don’t request such information through pop-ups.
5. Don’t Trust Caller ID
- Spoofed Caller ID: Be aware that phone calls can also be part of phishing attempts. Cybercriminals can spoof caller ID information to make it appear as if they are calling from a trusted organization. If you receive a call that seems suspicious, hang up and contact the organization directly using official contact information.
Protecting Yourself from Phishing:

Keep Your Software Updated:
- Regular Updates: Ensure your operating system, antivirus software, web browsers, and all applications are regularly updated. Updates often contain security patches that address known vulnerabilities.
- Automatic Updates: Enable automatic updates whenever possible to ensure you’re always running the latest, most secure versions of your software.
Exercise Caution with Links and Downloads:
- Hover Over Links: Before clicking on any link in an email or on a website, hover your mouse pointer over it to view the actual URL. Ensure that it matches the expected destination.
- Avoid Downloading Suspicious Attachments: Do not download attachments or files from untrusted sources, especially if you weren’t expecting them.
- Use a URL Scanner: Consider using URL scanning tools or browser extensions that can help identify potentially malicious websites.
Install a Reliable Antivirus Program:
- Choose Reputable Software: Invest in a reputable antivirus program that includes anti-phishing features. Ensure it is regularly updated to stay ahead of emerging threats.
- Regular Scanning: Schedule regular scans of your computer to detect and remove malware or potential threats.
Secure Your Wi-Fi Network:
- Strong Passwords: Protect your home Wi-Fi network with a strong, unique password to prevent unauthorized access.
- Encryption: Enable WPA3 encryption if your router supports it to enhance network security.
Be Wary of Unsolicited Requests:
- Don’t Share Personal Information: Avoid sharing personal or financial information via email, text, or phone calls, especially when the request is unsolicited.
- Verify Requests: If you receive a request for sensitive information or payment, contact the organization directly using their official website or phone number to confirm the request’s legitimacy.
Conclusion:
Phishing poses a persistent and evolving threat in the digital landscape. However, armed with knowledge and vigilance, you can defend yourself against these deceitful tactics. By understanding the mechanics of phishing, recognizing red flags, and adopting strong security practices like using unique passwords, keeping software up to date, and staying cautious with links and downloads, you can significantly reduce your vulnerability to these malicious attacks. Education is key, and staying informed about the latest phishing trends is your best defense.
FAQs:
What are common red flags for identifying phishing attempts?
Common red flags include unsolicited emails, urgent or threatening language, mismatched URLs in links, misspelled words or grammatical errors in emails, and requests for personal information via email.
How can I verify the sender’s identity in an email?
To verify a sender’s identity, check the sender’s email address carefully for slight variations. Additionally, contact the organization directly using their official website or phone number to confirm the legitimacy of any requests for personal information or payments.
Why is keeping software updated important in avoiding phishing attacks?
Outdated software can have known vulnerabilities that cybercriminals can exploit. Keeping your operating system, antivirus software, and applications up to date ensures these vulnerabilities are patched, reducing the risk of a successful phishing attack.
Is antivirus software effective in preventing phishing attacks?
While antivirus software can help detect and prevent some phishing attempts, it is not foolproof. Phishing attacks are becoming more sophisticated, so it’s essential to combine antivirus software with good security practices and user awareness.
