Introduction
Definition Of Hashing
Hashing is a process of converting digital information into a fixed-length code or value that represents the original data. This technique is commonly used in cryptography to ensure data integrity, which means that the data has not been tampered with during transmission or storage. Hashing algorithms operate on messages of arbitrary length and produce fixed-size outputs known as hash values or message digests.
Importance Of Hashing In Data Encryption
Hashing ensures secure data storage and transmission by creating an irreversible representation of the original data that can only be decrypted using specific algorithms. Hash values are commonly used in password verification systems, file integrity checks, digital signatures, and other security applications.
One major benefit of hashing in data encryption is its ability to detect tampering or data manipulation. Since any changes made to the original data will result in a different hash value, it becomes easier to identify if someone has attempted to modify the information illicitly. Moreover, hashing allows for efficient retrieval and comparison of large volumes of data in real time without revealing sensitive information.
understanding hashing fundamentals is essential for anyone who wants to learn about data encryption techniques. With this knowledge, individuals can implement more robust security measures for their sensitive information and protect themselves against cyber threats such as identity theft and hacking attacks.
Understanding Hash Functions
What Are Hash Functions?
Hash functions are mathematical algorithms that take in a set of data and output a fixed-size string of characters. These functions are commonly used for data encryption, as they can generate unique codes for each input, allowing for secure storage and retrieval of sensitive information. Hash functions are designed to be one-way, meaning it’s nearly impossible to reverse engineer an input from its hash code.
Characteristics Of Hash Functions
The key characteristics of a hash function include collision resistance, pre-image resistance, and an avalanche effect.
Collision resistance refers to the ability of the hash function to produce unique outputs for different inputs. This property is crucial in ensuring that two different inputs do not have the same hash value.
Pre-image resistance refers to the difficulty in determining input data from its corresponding hash value. In other words, given a hash value, it should be computationally infeasible to find out what input was used to generate it.
The avalanche effect means that even minor changes made to the input data will result in significant changes in the output or message digest produced by the hash function. This characteristic ensures that any modifications made during transmission or storage can be easily detected by comparing hashes before and after modification.
Commonly Used Hash Functions
There are several commonly used hash functions that provide different levels of security and performance. MD5 (Message Digest 5) is one of the oldest hash functions still in use today. It produces a 128-bit hash value that has been found to have some vulnerabilities. SHA-1 (Secure Hash Algorithm 1) also generates a 160-bit hash value but has been found to have weaknesses as well.
On the other hand, SHA-256 (Secure Hash Algorithm 256) generates a more secure 256-bit hash value that is widely used for digital signatures, SSL/TLS certificates, and other security protocols. Other popular hash functions include BLAKE2, Keccak/SHA-3, and Argon2 – all designed with varying levels of security features depending on their intended use case.
How Hashing Works In Data Encryption?
Hashing vs Encryption
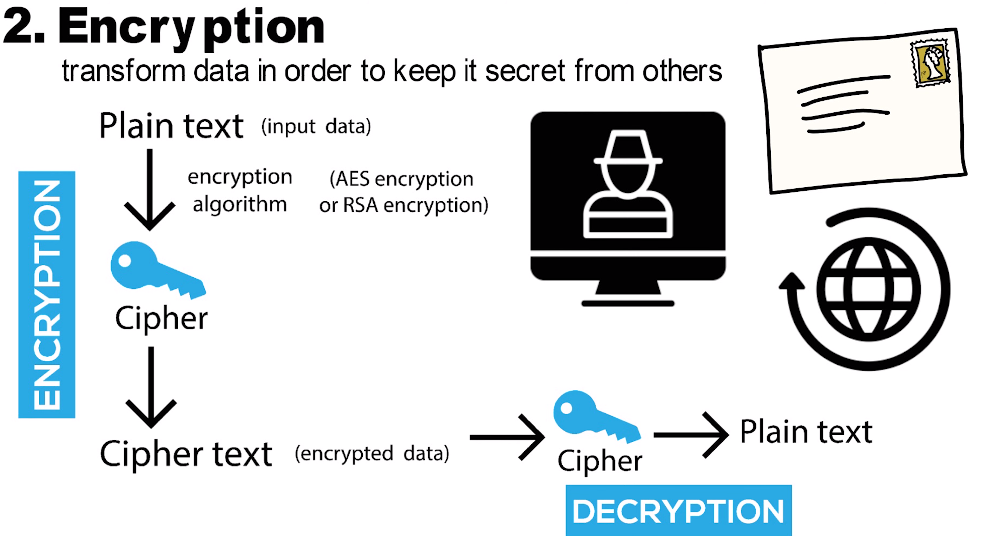
Hashing is primarily used to verify if the data has been tampered with or not, while encryption is used to keep the information confidential. In hashing, an algorithm generates a fixed-size output (hash) from any given input message. The hash value is unique for each input, and even a small change in the input will result in a vastly different hash value. Therefore, hashing is widely used to check if two sets of data are identical or not – such as checking if a downloaded file matches its original version.
On the other hand, encryption involves converting plain text into ciphertext using an algorithm that can only be decrypted with a key or password known by authorized parties. Unlike hashing, encryption provides confidentiality of data allowing only authorized individuals to read it.
Benefits Of Hashing In Data Encryption
One of the primary benefits of hashing is that it ensures data integrity. By generating a unique hash value for each piece of input data, any changes made to the original input will result in an entirely different hash value. Therefore, if someone tries to tamper with the original data during transmission or storage, this manipulation will be detectable by comparing the original hash value with its new counterpart.
Another significant benefit of hashing is that it allows for password verification without storing passwords directly. When a user creates a password, their password gets hashed and stored on servers instead of being saved as plain text. When they enter their password again later on, it gets hashed once more and compared against what was previously stored in order to authenticate them.
Types Of Hash Functions
Cryptographic Hash Functions
A cryptographic hash function is a one-way mathematical algorithm that takes any input and produces a fixed-size output, called a hash. Hashing is used to verify the integrity of data, ensuring that it has not been tampered with during transmission or storage. Even small changes to the input will produce vastly different hashes, making it practically impossible for an attacker to reverse-engineer the original input.
Non-Cryptographic Hash Functions
Non-cryptographic hash functions are used in various applications where the security of data is not a primary concern. These hash functions are faster and simpler than cryptographic hash functions, which makes them an ideal choice for applications like checksums, error detection codes, and indexing. Non-cryptographic hash functions do not provide any kind of encryption or secure hashing of data but they can still be useful in certain situations.
One example where non-cryptographic hash functions can be used is in content-addressable storage systems. These systems use hashes to identify unique pieces of content, such as images or video files. Since these hashes are only required to be unique within the system, non-cryptographic hashes can provide sufficient performance without compromising on accuracy.
Another application area for non-cryptographic hash functions is indexing databases. Hash indexes work by mapping keys to a specific location within the database using a hashing function. Non-cryptographic hashes offer faster processing and less memory overhead compared to cryptographic hashes while still maintaining good collision resistance properties necessary for indexing databases.
Common Applications Of Hashing
Password Storage

The main objective of hashing is to ensure that the original password cannot be retrieved from the stored hash value. Hashing provides an added layer of security to protect user credentials in case of a data breach.
Digital Signatures

To create a digital signature, the original document is first hashed using an encryption algorithm such as SHA-256. The resulting hash value is then encrypted using the private key of the person signing the document. This creates a unique digital signature that can only be decrypted using their public key. When someone receives a digitally signed document, they can use this public key to decrypt the signature and confirm its authenticity.
Message Authentication Codes (Macs)
Message authentication codes (MACs) are a type of cryptographic algorithm that verifies the integrity and authenticity of a message. The primary purpose of MACs is to detect any unauthorized changes to the data being transmitted and ensure that it was not tampered with during transit. MACs use symmetric-key cryptography, which means that both parties involved in communication share the same secret key.
There are several types of MAC algorithms available, including HMAC, CBC-MAC, and CMAC. HMAC (Hash-based Message Authentication Code) is one of the most commonly used MAC algorithms in modern cryptography. It uses a cryptographic hash function along with a secret key to generate a code that can verify the integrity and authenticity of data.
Integrity Checks
One common method for performing an integrity check is by using a hash function. A hash function takes a block of data and generates a fixed-size digest, which can then be used to verify whether the original data has been modified at any point. The recipient can generate their own hash value and compare it with the sender’s value to ensure that no changes have been made.
Hashing Attacks And Vulnerabilities
Collision Attacks
Collision attacks are a type of cyber attack that involves finding two different inputs that produce the same output when hashed. This is a major security concern in data encryption because it allows attackers to bypass security measures and gain unauthorized access to sensitive information.
There are several types of collision attacks, including birthday attacks and brute force attacks. Birthday attacks involve finding two inputs with the same hash value by generating random inputs until a match is found. Brute force attacks involve systematically testing all possible input combinations until a collision occurs.
Preimage Attacks
Preimage attacks are a type of cryptographic attack that targets the output of a hash function. The goal of such an attack is to find an input value that produces the same hash as a given output value, without knowing the original input. A successful preimage attack would allow an attacker to break the integrity and authenticity of digital signatures, message authentication codes (MACs), and other security protocols that rely on hashing.
There are two types of preimage attacks: first preimage and second preimage. First preimage attacks aim to find any input value that generates a specific hash output. On the other hand, second preimage attacks aim to find another input value that produces the same hash as a known input value. Both types of these attacks can be incredibly damaging in data encryption because they can compromise sensitive information and undermine trust in digital security systems.
Birthday Attacks
A birthday attack is a type of cryptographic attack that exploits the probability of two random inputs producing the same output value in hash functions.
To put it simply, a hacker can generate multiple random input values until they find two inputs that produce the same output value. This process is called collision detection, and once the hacker finds these matching pairs, they can manipulate them to gain unauthorized access to sensitive data.
Despite its name, birthday attacks are not limited to birthdays but rather rely on mathematical probabilities similar to the likelihood of individuals sharing a birthday in a group. To prevent such attacks from happening, developers use various techniques like salting or using longer bit lengths for hashing algorithms.
Salting And Its Role In Preventing Attacks
Salting involves adding a random string of characters to the input before it is hashed, making it much harder for attackers to crack.
Salting can significantly increase the security of passwords by not only making them more difficult to guess but also by reducing the likelihood of two users having identical hashed passwords. In addition, salting can also help protect against precomputed hash attacks where attackers create a table of precalculated hashes for commonly used passwords or combinations.
Best Practices For Implementing Hashing In Data Encryption
Choosing The Right Hashing Algorithm
Choosing the right hashing algorithm depends on factors such as the required level of security, performance needs, compatibility with existing systems, etc. As technology continues to evolve and new vulnerabilities emerge, staying up-to-date on current best practices in choosing a hashing algorithm is critical for maintaining secure data encryption processes.
Implementing Salting
Implementing salting is relatively easy and should be done in combination with a strong hashing algorithm like bcrypt or scrypt. The salt can be generated using a cryptographically secure pseudorandom number generator or by using a predefined sequence stored securely on the server.
It’s important to note that salting does not provide complete protection against all types of attacks, but it significantly increases the security of password storage. When implementing salting, it’s also essential to ensure that the salt value is stored securely alongside the hashed password to prevent unauthorized access.
Recommendations For Secure Hashing
It is important to use a hashing algorithm that is considered secure by industry standards. Some recommended algorithms include SHA-256, SHA-3, and BLAKE2. These algorithms have undergone extensive testing and analysis to ensure their security.
Keep up with updates and patches for any software or systems that utilize hashing. New vulnerabilities are discovered all the time, so staying on top of updates can help prevent any potential security breaches. Regularly updating your system’s security measures can make sure that your hashed passwords stay safe from malicious attacks by hackers who seek access to your organization’s confidential information without proper authorization.
Conclusion
Hashing is a fundamental aspect of data encryption that plays an essential role in securing sensitive information. By converting plain text into a unique string of characters using a one-way algorithm, hashing ensures that data cannot be easily reverse-engineered or tampered with. It also allows for quick and efficient comparisons between two sets of data without the need to compare the entire dataset.
However, it’s essential to note that while hashing is an effective way to secure data, it does have its limitations. For example, hash collisions can occur when two different inputs generate the same hash value, which can lead to security vulnerabilities. It’s also important to stay up-to-date on any new developments or threats related to hashing techniques and algorithms.
Frequently Asked Questions (FAQs)
Can A Hashed Password Be Decrypted?
While it might seem impossible to decrypt a hashed password, there are some techniques that attackers can use to try and break through the encryption. One such technique is called “brute-force attack,” which involves guessing every possible combination until the correct one is found. However, this method can take up an enormous amount of time and resources.
Another approach attempted by hackers is using precomputed tables or rainbow tables containing hashes of common passwords and their corresponding hash values. By matching these values against an encrypted password, an attacker may be able to determine its original form.
What Is The Purpose Of Salting In Hashing?
The purpose of salting is to make it difficult for attackers to use precomputed tables or rainbow attacks to crack passwords.
When a password or other sensitive information is hashed, it is converted into a fixed-length string of characters that cannot be reversed. However, if two users have the same password, their hash values will also be the same. This makes it easier for attackers who have access to these hash values to identify identical passwords.
How Can I Choose The Right Hashing Algorithm For My Data Security Needs?
Determine the level of security required for your data. Some algorithms provide a higher level of security than others, so it’s important to be aware of their strengths and weaknesses.
Another key factor is the speed at which the algorithm can process data. While some algorithms are slower but more secure, others are faster but less secure. Depending on your specific needs, you may prioritize one over the other.
Consider compatibility with existing systems and tools. If you’re working with legacy systems or third-party software that require a specific hashing algorithm, it may not be feasible or practical to switch to a different one.
