Importance of Data Security
Data security is of utmost importance in today’s digital age, where sensitive information is stored and transmitted electronically. Here are some reasons why data security is crucial:
1. Protecting confidential information: Data security measures are necessary to protect sensitive and confidential information such as personal identification details, financial information, and trade secrets from unauthorized access, theft, or misuse.
2. Preventing cyber attacks: Cyber attacks are becoming increasingly sophisticated, and data breaches can have serious consequences for businesses and individuals.
Common Threats to Data Security
Here are some common threats to data security:
1. Malware: Malware is a type of software that is designed to harm or disrupt computer systems. It can be used to steal sensitive information, damage files, or take control of the system.
2. Phishing attacks: Phishing is a type of social engineering attack that involves tricking people into providing sensitive information such as login credentials or financial information.
3. Insider threats: Insider threats occur when someone within an organization intentionally or unintentionally.
Strengthening Your Passwords

To strengthen your passwords, you can follow these tips:
1. Use a combination of uppercase and lowercase letters, numbers, and symbols.
2. Avoid using easily guessable information such as your name, birthdate, or common words.
3. Use a unique password for each account to prevent all your accounts from being compromised if one password is breached.
4. Consider using a password manager to generate and store strong passwords for you.
Importance of Strong Passwords
Having strong passwords is crucial for protecting your personal and sensitive information online. Without strong passwords, hackers can easily access your accounts and steal your data, such as financial information, social security numbers, and even your identity. Strong passwords make it more difficult for hackers to guess or crack your password, making it harder for them to gain unauthorized access to your accounts. By following the tips mentioned above, you can create strong passwords that will help keep your accounts secure.
Tips For Creating Strong Passwords
1. Use a mix of upper and lowercase letters, numbers, and symbols.
2. Avoid using common words or phrases, such as “password” or “123456”.
3. Use a longer password, ideally 12 characters or more.
4. Avoid using personal information, such as your name or birthdate.
5. Consider using a password manager to generate and store strong passwords.
6. Use different passwords for each account to prevent a single breach from compromising multiple accounts.
Password Manager Tools

Here are some password manager tools that you can consider using:
1. LastPass: It generates and stores strong passwords, and can also autofill login credentials for you.
2. Dashlane: It offers similar features to LastPass, including password generation and autofill.
3. 1Password: It offers password generation and storage, as well as a feature that checks if any of your passwords have been compromised in a data breach.
Implementing Two-Factor Authentication
Two-factor authentication (2FA) is an additional layer of security that requires you to provide two forms of identification before accessing your account. This can include something you know (like a password) and something you have (like a security token or your mobile phone).
Types of Two-Factor Authentication
There are several types of two-factor authentication that you can use to secure your accounts. Some of the most common types include:
1. SMS or Text Message Verification: This involves receiving a code via text message that you must enter in addition to your password to gain access to your account.
2. Authenticator Apps: These apps generate a unique code that you must enter in addition to your password to access your account. Popular authenticator apps include Google Authenticator, Microsoft Authenticator, and Authy.
Setting Up Two-Factor Authentication
It is a great way to add an extra layer of security to your accounts. To set it up, you’ll need to go to your account settings and look for the option to enable two-factor authentication. From there, you can choose which type of verification method you want to use and follow the prompts to set it up. Make sure to keep your phone number and/or authenticator app secure, as they will be the key to accessing your account.
Regularly Updating Your Software
Regularly updating your software is crucial for maintaining the security of your devices. Software updates often include important security patches that fix vulnerabilities that could be exploited by hackers. To ensure that your software is up-to-date, you should enable automatic updates whenever possible. You can also manually check for updates in your device’s settings or through the software’s website. It is important to note that you should only download updates from trusted sources to avoid downloading malware or other malicious software.
Automatic Vs. Manual Updates
Automatic updates are a convenient way to ensure that your software is always up-to-date without requiring any action on your part. This is especially useful for busy users who may forget to manually check for updates. However, some users may prefer to manually update their software to have more control over the process. When it comes to security updates, it is recommended to enable automatic updates to ensure that any vulnerabilities are patched as soon as possible. For non-security updates, the choice between automatic and manual updates is up to the user.
Updating Individual Applications
To update individual applications, users can typically go to the application’s settings or preferences menu and look for an option to check for updates. Some applications may also have a built-in update checker that will automatically prompt the user to update when a new version is available. It is important to regularly check for updates to ensure that applications are running smoothly and to take advantage of new features and bug fixes. Additionally, keeping all software up to date can help prevent security vulnerabilities and protect against potential threats.
Using Antivirus and Anti-Malware Software
It’s important to have antivirus and anti-malware software installed on your computer to protect against viruses, malware, and other malicious software. There are many options available, both free and paid, and it’s important to choose one that fits your needs and budget. Some popular options include Avast, AVG, Norton, and McAfee. It’s also important to keep your antivirus and anti-malware software up to date to ensure that it can effectively protect against the latest threats.
Types of Malware
Malware, short for “malicious software,” is a broad term that refers to any type of software designed to harm a computer system or steal sensitive information. Some common types of malware include:
1. Viruses: These are programs that can replicate themselves and spread from one computer to another. They can cause damage to files, software, and hardware.
2. Trojans: These are programs that appear to be legitimate but contain hidden malicious code. They can be used to steal sensitive information.
Benefits of Antivirus And Anti-Malware Software
Antivirus and anti-malware software are essential tools for protecting your computer system from various types of malware. Here are some benefits of using antivirus and anti-malware software:
1. Protection against viruses and malware: Antivirus and anti-malware software can detect and remove viruses, Trojans, spyware, adware, and other types of malware that can harm your computer system.
2. Real-time protection: Most antivirus and anti-malware software offer real-time protection, which can be beneficial for protecting data.
Choosing The Right Software
Choosing the right antivirus and anti-malware software can be a daunting task, as there are many options available in the market. Here are some tips to help you choose the right software for your computer system:
1. Compatibility: Make sure that the software you choose is compatible with your operating system and hardware specifications.
2. Features: Look for software that offers a range of features such as real-time protection, automatic updates, and scheduled scans.
3. Reputation: Choose software from reputable and well-known companies that have a track record of providing reliable and effective protection.
4. User-Friendliness: Choose software that is easy to install and use, with a simple and intuitive interface.
5. Customer Support: Look for software that offers good customer support, with easy access to help and support resources.
6. Price: Consider the cost of the software, but don’t compromise on quality for the sake of a lower price. Look for software that
Setting Up User Accounts
Setting up user accounts can be a crucial task for any organization or business. Here are some tips to make the process smoother:
1. Determine the level of access required for each user: Before creating user accounts, it’s important to decide what level of access each user needs. This will help you create appropriate user roles and permissions.
2. Use strong passwords: Make sure to use strong passwords for each user account. A strong password should be at least 8 characters long and include a combination of uppercase and lowercase.
3. Restrict physical access to sensitive areas: If your business deals with sensitive information, it’s important to restrict physical access to areas where that information is stored. This can be done through keycard access or security personnel.
4. Implement two-factor authentication: Two-factor authentication adds an extra layer of security to user accounts by requiring a second form of verification, such as a code sent to a user’s phone.
Protecting Your Network
1. Use a firewall: A firewall is a network security system that monitors and controls incoming and outgoing network traffic based on predetermined security rules. It can help prevent unauthorized access to your network.
2. Keep software up to date: Regularly updating software can help patch security vulnerabilities and prevent cyber attacks. This includes operating systems, anti-virus software, and other applications.
3. Use strong passwords: Strong passwords can help prevent unauthorized access to network devices and user accounts.
Understanding Network Security
Network security refers to the measures taken to protect computer networks from unauthorized access, theft, or damage. It involves a combination of hardware and software technologies, as well as policies and procedures designed to safeguard the confidentiality, integrity, and availability of network resources. Effective network security requires a multi-layered approach that includes perimeter defence, access control, encryption, and monitoring. Organizations need to have a comprehensive security plan in place to protect against a variety of threats, including malware, and phishing attacks.
Tools For Securing Your Network
Several tools and technologies can be used to secure a network. Some of these include:
1. Firewall: A firewall is a network security device that monitors and controls incoming and outgoing network traffic based on predetermined security rules.
2. Antivirus Software: Antivirus software is designed to detect and remove malware from a computer system.
3. Virtual Private Network (VPN): A VPN is a secure tunnel between two or more devices that allows for secure communication over the internet.
Being Cautious with Email and Internet Use
To ensure the security of a network, it is important to be cautious with email and internet use. Some tips include:
1. Avoid opening suspicious emails or clicking on links from unknown sources.
2. Use strong passwords and change them frequently.
3. Keep software and operating systems up to date with the latest security patches.
4. Use two-factor authentication whenever possible.
5. Avoid using public Wi-Fi networks for sensitive activities.
By implementing these measures, you can help to protect your network from potential security
Common Email And Internet Scams
There are several common email and internet scams that people should be aware of, including:
1. Phishing scams: These scams involve fraudulent emails or websites that trick people into providing sensitive information such as usernames, passwords, and credit card numbers.
2. Malware: Malware is malicious software that is designed to damage or disrupt computer systems. It can be delivered through email attachments, downloads, or links.
3. Fake websites: Cybercriminals create fake websites that look like legitimate ones to trick people.
Best Practices For Email And Internet Use
Here are some best practices for email and internet use to help protect against phishing scams, malware, and fake websites:
1. Be cautious of emails or messages from unknown senders, especially if they contain suspicious links or attachments.
2. Verify the authenticity of websites by checking the URL and looking for security indicators such as HTTPS and a padlock icon.
3. Use strong and unique passwords for all accounts and enable two-factor authentication whenever possible.
4. Keep software and operating systems up to date.
FAQs
What Are The Consequences Of Poor Data Security?
Poor data security can have serious consequences, such as identity theft, financial loss, and damage to one’s reputation. It can also result in the loss of sensitive information, such as personal and confidential data, which can be used for fraudulent purposes or sold on the dark web. In some cases, poor data security can even lead to legal action or fines for businesses that fail to protect their customers’ data.
How Can I Test The Strength of My Passwords?
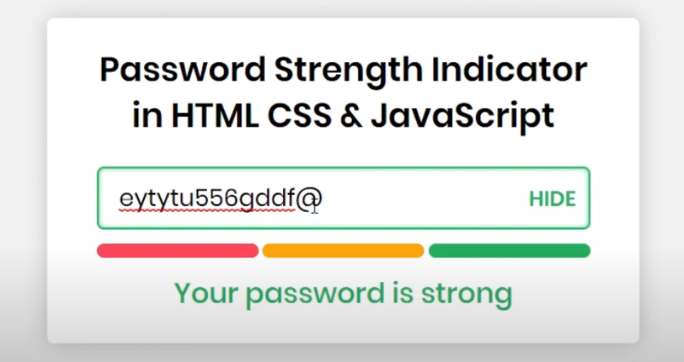
There are several ways to test the strength of your passwords. One common method is to use a password strength meter, which is a tool that analyzes your password and rates its strength based on factors such as length, complexity, and uniqueness. Another way is to use a password cracking tool, which is a program that attempts to guess your password by using various techniques, such as dictionary attacks and brute force attacks.
Do I Need To Pay For Antivirus Software?
It depends on your specific needs and preferences. There are both free and paid antivirus software options available, and each has its own set of features and benefits. Free antivirus software can provide basic protection against common threats, while paid antivirus software typically offers more advanced features such as real-time protection, firewall protection, and enhanced malware detection. Ultimately, the decision to pay for antivirus software will depend on your individual needs and budget.
How Often Should I Back Up My Data?
It is recommended to back up your data regularly, ideally daily. This ensures that in the event of a data loss or system failure, you will have a recent copy of your important files and documents. You can back up your data to an external hard drive, cloud storage service, or other backup solution. It is also a good idea to test your backups periodically to ensure that they are working properly and that you can restore your data if needed.
Can I Rely Solely on Software To Protect My Data?
While software can certainly be a helpful tool in protecting your data, it’s important to note that it should not be relied upon solely. Hardware failures, natural disasters, and other unforeseen events can still result in data loss even with the best software in place. This is why it’s important to have a comprehensive backup plan that includes both software and hardware solutions, as well as regular testing and maintenance to ensure that your data is properly protected.
Conclusion
In conclusion, staying safe online is important in today’s digital age. By being aware of the risks and taking the necessary precautions, such as being cautious of unknown senders, verifying website authenticity, using strong passwords and keeping software up to date, we can protect ourselves from phishing scams, malware and fake websites.
