End-to-end encryption (E2E) is a robust security protocol that ensures only the sender and intended recipient can read a message, achieved through a process involving key generation, data encryption, secure transmission, and decryption. E2E encryption is widely used in messaging apps, email services, voice and video calls, cloud storage, file-sharing services, collaboration tools, web browsers, and even some social media platforms.
Understanding End-to-End Encryption
End-to-end encryption (E2E) is a robust security protocol that ensures only the sender and intended recipient of a message can read its content. This means that even if the data is intercepted by malicious actors or intercepted during transmission, it remains indecipherable to anyone without the encryption keys.
How Does End-to-End Encryption Work?
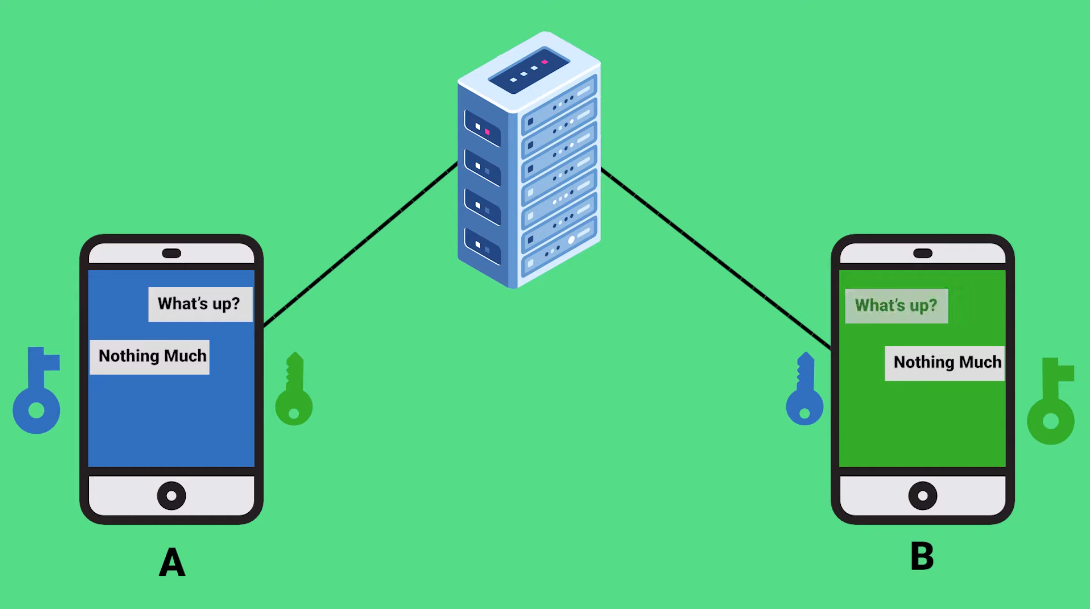
End-to-end encryption operates by encrypting data at its source and decrypting it only at its intended destination.
- Key Generation
The process begins with the generation of a unique encryption key. This key is the linchpin of end-to-end encryption, and it’s the element that makes your messages secure. Each conversation or session has its own distinct key, adding an extra layer of security. - Data Encryption
Once the key is in place, your data is encrypted at the sender’s end before it begins its journey over the internet. Encryption transforms your message or files into a format that appears as gibberish to anyone who intercepts it. This ensures that even if your communication is compromised, the intercepted data remains indecipherable without the encryption key. - Secure TransmissionThe encrypted data is then transmitted over the internet as it normally would be. During this stage, it’s essential to understand that the service provider facilitating the communication does not have access to the encryption key. This means that the provider cannot decrypt your data, ensuring your privacy.
- Decryption at the Receiver’s End
Upon reaching the intended recipient, the encrypted data is received. The recipient’s device possesses the decryption key necessary to transform the gibberish back into the original, understandable message or file. This decryption process happens seamlessly and instantly for the recipient, ensuring the privacy of your communication. - Encryption Algorithms
The success of end-to-end encryption relies on the strength of encryption algorithms. These algorithms are complex mathematical formulas that dictate how data is encrypted and decrypted. Modern encryption algorithms are highly secure and virtually impossible for unauthorized parties to crack. - Key Management
Key management is a critical aspect of end-to-end encryption. The keys must be kept secure and confidential. In many cases, the keys are stored locally on the devices of the sender and receiver, making them less susceptible to interception. - Forward Secrecy
Forward secrecy is an additional security feature of end-to-end encryption. It ensures that even if an encryption key is compromised in the future, past communications remain secure because they were encrypted with different keys. This makes it extremely challenging for attackers to access historical data.
The Role of Encryption Keys:
Public and Private Keys
End-to-end encryption relies on a pair of keys: a public key and a private key. The public key is freely shared and used to encrypt data, while the private key is kept secret and used to decrypt the data.
Key Exchange Protocols
The challenge lies in securely exchanging these keys. Various key exchange protocols, like Diffie-Hellman and RSA, facilitate this process, ensuring that only the recipient can decrypt the data.
Applications of End-to-End Encryption
End-to-end encryption has found applications in various digital communication channels and services:
- Messaging Apps
End-to-end encryption is a feature of many popular messaging applications, including WhatsApp, Signal, and Telegram. When you send a message through these platforms, it’s encrypted on your device and can only be decrypted by the intended recipient. This ensures that your conversations remain private and secure. - Email Services
Certain email providers offer end-to-end encryption as an option for securing email communications. One notable example is ProtonMail, which provides end-to-end encryption for both the content of the email and any attachments. This means that only the recipient with the decryption key can read the email, protecting sensitive information. - Voice and Video Calls
End-to-end encryption is also used in voice and video calling applications like Signal and FaceTime. When you make a call using these services, the audio and video data is encrypted during transmission, preventing eavesdropping by third parties. - Cloud Storage
Some cloud storage services incorporate end-to-end encryption to protect the files and documents you store on their platforms. Examples include Tresorit and pCloud. With this level of encryption, even the storage provider cannot access your data without your encryption key. - File Sharing Services
File-sharing services like Sharefile and SpiderOak employ end-to-end encryption to secure files that are shared between users. This means that only those with the appropriate decryption key can access the shared files, maintaining data privacy. - Collaboration Tools
In the realm of online collaboration, tools like Slack and Microsoft Teams often offer end-to-end encryption options for sensitive conversations and file sharing within the platform. This ensures that confidential business discussions and documents are protected. - Web Browsers
Certain web browsers, such as Brave, include end-to-end encryption features to enhance user privacy while browsing the internet. These browsers employ encryption to secure your browsing data, making it more challenging for third parties to track your online activities. - Social Media Platforms
Some social media platforms are beginning to incorporate end-to-end encryption for private messaging features. For example, Facebook-owned WhatsApp offers end-to-end encryption for its private chats.
The Importance of End-to-End Encryption

Protecting Privacy
In an era of increasing surveillance and data breaches, E2E encryption is a potent tool for safeguarding your personal information.
Secure Business Communication
For businesses, E2E encryption ensures that sensitive corporate data and communications are shielded from prying eyes.
Legal and Ethical Implications
The use of E2E encryption has sparked debates on privacy versus national security, raising important legal and ethical questions.
The Potential Implications of End-to-End Encryption:
Law Enforcement and National Security
End-to-end encryption can make it challenging for law enforcement and intelligence agencies to access communications for legitimate investigative purposes, raising debates about balancing security and privacy.
Misuse by Criminals
Criminals may exploit end-to-end encryption for illicit activities, knowing that their communications are shielded from surveillance.
Lost Data Access
If you forget your encryption key, you risk losing access to your own data, as there’s no way to recover it without the key.
Future of End-to-End Encryption:
Advancements in Quantum Computing
The rise of quantum computing poses a potential threat to current encryption methods, driving the need for quantum-resistant encryption algorithms.
Evolving Regulations
As governments grapple with encryption’s impact on security and privacy, regulations and policies regarding its use are likely to evolve.
Conclusion
End-to-end encryption (E2E) ensures that our online communications remain confidential, shielding them from prying eyes and potential cyber threats. While E2E encryption has found widespread application in messaging apps, email services, and various other digital communication channels, it is not without its challenges. Debates about the balance between privacy and national security, the potential misuse by criminals, and the looming threat of quantum computing advancements are shaping the future landscape of E2E encryption.
Frequently Asked Questions:
What are Public and Private Keys in End-to-End Encryption?
In E2E encryption, a pair of keys is used: a public key and a private key. The public key is freely shared and used to encrypt data, while the private key is kept secret and used to decrypt the data.
How are Encryption Keys Exchanged Securely?
Various key exchange protocols, such as Diffie-Hellman and RSA, facilitate the secure exchange of encryption keys. These protocols ensure that only the intended recipient can decrypt the data.
Where is End-to-End Encryption Used?
E2E encryption is used in various digital communication channels and services, including messaging apps, email services, voice and video calls, cloud storage, file-sharing services, collaboration tools, web browsers, and even some social media platforms.
What is Forward Secrecy in End-to-End Encryption?
Forward secrecy is an additional security feature of E2E encryption. It ensures that even if an encryption key is compromised in the future, past communications remain secure because they were encrypted with different keys. This makes it extremely challenging for attackers to access historical data.
