What is TLS Encryption?
TLS (Transport Layer Security) encryption is a protocol that provides privacy and data integrity between two communicating applications. It is commonly used to secure communication over the internet, such as when you access a website or send an email. TLS encryption works by establishing a secure connection between the two applications, encrypting the data that is transmitted between them, and verifying the identity of the parties involved.
Why is TLS Encryption Important?
TLS encryption is important because it helps protect sensitive information from unauthorized access and tampering. Without encryption, data transmitted over the internet can be intercepted and read by attackers, potentially exposing sensitive information such as passwords, credit card numbers, and personal information. TLS encryption helps ensure that only authorized parties can access the data being transmitted and that the data has not been tampered with during transmission. This is particularly important for businesses and organizations that handle sensitive customer data, as well as for individuals who want to protect
Brief History of TLS Encryption
TLS (Transport Layer Security) encryption is a protocol used to secure communication over the internet. It was developed as an improvement to SSL (Secure Sockets Layer) encryption, which was widely used in the early days of the Internet. The first version of TLS was introduced in 1999, and since then, several versions have been released to address security vulnerabilities and improve performance.
Overview of the TLS Handshake
The TLS handshake is the process by which a client and server establish a secure connection. During the handshake, the client and server negotiate the encryption algorithms and keys to be used for the session. The TLS handshake is a critical component of the TLS protocol, as it ensures that the client and server can communicate securely and that the data exchanged between them is protected from eavesdropping and tampering. To protect your online communication, it’s important to ensure that the websites you visit use TLS encryption.
The Role of Certificates in TLS Encryption
Certificates play a crucial role in TLS encryption. They are used to verify the identity of the server and establish a secure connection between the client and the server. When a client connects to a server using TLS, the server sends its digital certificate to the client. The certificate contains the server’s public key, which is used by the client to encrypt data that will be sent to the server.
Understanding Public Key Cryptography
Public key cryptography is a type of encryption that uses two keys – a public key and a private key. The public key is used to encrypt data, while the private key is used to decrypt it. This method is used in TLS encryption to ensure that only the intended recipient can read the data being transmitted. The public key is shared with anyone who wants to send encrypted data, while the private key is kept secret by the owner.
Symmetric vs Asymmetric Encryption
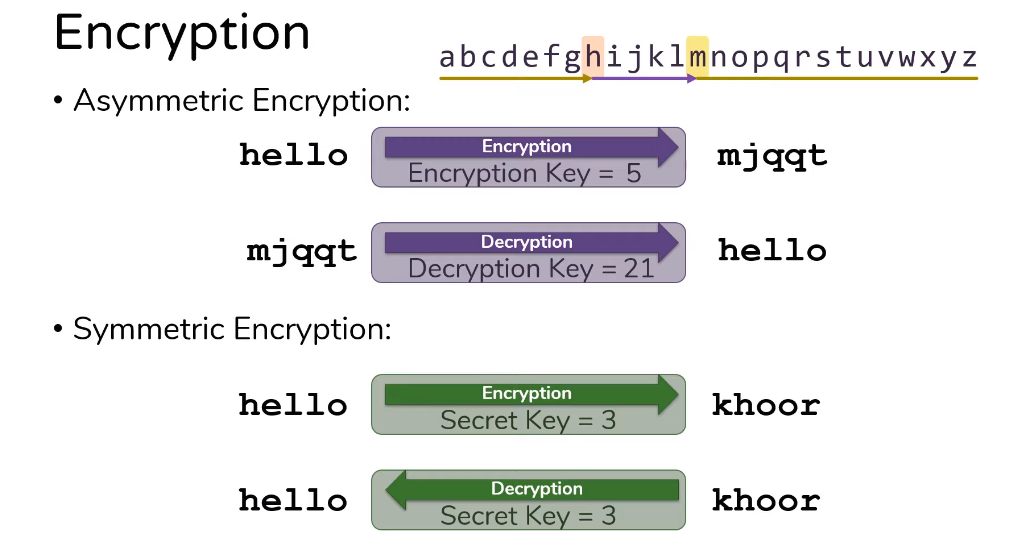
Symmetric encryption uses the same key to both encrypt and decrypt data. This means that anyone who has access to the key can decrypt the data. Asymmetric encryption, on the other hand, uses two different keys – a public key and a private key – for encryption and decryption. This makes it more secure, as the private key is kept secret by the owner and cannot be easily accessed by others.
Key Exchange in TLS Encryption
In TLS encryption, the key exchange process is used to securely exchange the keys needed for symmetric encryption. This process involves the client and server agreeing on a shared secret key that will be used for encrypting and decrypting data during the session. The key exchange process typically uses asymmetric encryption, with the server’s public key being used to encrypt the shared secret key, which is then decrypted using the server’s private key. This ensures that only the server can access the shared secret key, making the encryption more
Strengths and Weaknesses of TLS Encryption
TLS encryption provides a strong level of security for data transmission over the internet. Some of its strengths include:
- Confidentiality: TLS encryption ensures that data transmitted between the client and server is kept confidential, as it cannot be intercepted and read by a third party.
- Integrity: TLS encryption ensures that data transmitted between the client and server has not been tampered with or modified in transit.
Advantages of TLS Encryption
In addition to the strengths mentioned above, there are several other advantages of TLS encryption:
- Authentication: TLS encryption provides authentication of the server to the client, ensuring that the client is communicating with the intended server and not an imposter.
- Compatibility: TLS encryption is widely used and supported by most web browsers, servers, and applications, making it a reliable and accessible form of encryption.
Limitations of TLS Encryption
In addition to its advantages, there are also some limitations of TLS encryption that should be considered:
- Vulnerabilities: While TLS encryption is generally considered secure, there have been vulnerabilities discovered in the past that could potentially compromise the security of encrypted communication.
- Performance: TLS encryption can add some overhead to communication, which can impact performance, particularly on high-traffic websites or applications.
- Configuration: Proper configuration of TLS encryption can be complex, and misconfigured encryption can lead to security vulnerabilities.
Common Attacks on TLS Encryption
Several common attacks on TLS encryption can compromise its security:
- Man-in-the-middle attacks: In this attack, an attacker intercepts communication between two parties and alters the messages being sent. This can be done by intercepting communication at a public Wi-Fi hotspot or by compromising a router.
- Cipher suite attacks: TLS uses a cypher suite to encrypt communication. If an attacker can compromise the cypher suite, they can potentially decrypt the communication.
Future of TLS Encryption
The future of TLS encryption is constantly evolving to keep up with new security threats and advancements in technology. Here are some potential developments:
Post-quantum cryptography: With the rise of quantum computers, TLS encryption may become vulnerable to attacks. Post-quantum cryptography is a new type of encryption that is resistant to quantum attacks and may become the new standard for TLS.
TLS Encryption 1.3 and Beyond
TLS Encryption 1.3 is already in use and offers improved security and performance compared to previous versions. However, there is always room for improvement.
Quantum Computing and TLS Encryption
Quantum computing is a potential threat to TLS encryption, as it can break traditional encryption methods. This has led to the development of post-quantum cryptography, as mentioned earlier. However, researchers are also exploring the use of quantum cryptography, which uses the principles of quantum mechanics to create unbreakable encryption. This could potentially revolutionize TLS encryption in the future.
Alternative Encryption Technologies
In addition to post-quantum cryptography and quantum cryptography, other alternative encryption technologies are being developed to enhance TLS encryption. One such technology is homomorphic encryption, which allows computations to be performed on encrypted data without decrypting it first. This could lead to more secure data processing and storage. Another technology is lattice-based cryptography, which uses mathematical structures called lattices to create secure encryption. Lattice-based cryptography is believed to be resistant to quantum attacks and has the potential to be a strong alternative.
TLS Encryption and the Internet of Things
TLS encryption is a widely used technology for securing internet communications. It ensures that data transmitted between two endpoints is encrypted and cannot be intercepted by anyone else. This technology is particularly important for the Internet of Things (IoT), which involves devices communicating with each other over the Internet. IoT devices are often vulnerable to security threats due to their limited processing power and memory. TLS encryption can help protect these devices by ensuring that the data they transmit is secure.
Conclusion
In conclusion, TLS encryption is a crucial technology for ensuring secure Internet communications. It plays a significant role in protecting sensitive data from being intercepted by unauthorized parties. With the increasing use of IoT devices, the need for TLS encryption has become more critical than ever before. As a writing assistant, I highly recommend incorporating TLS encryption in all internet communications to ensure the highest level of security.
FAQs
What is TLS Encryption?
TLS encryption is a technology that ensures secure Internet communications by encrypting data sent between two parties. It stands for Transport Layer Security and is commonly used in web browsing, email communication, and other online transactions. It is a crucial technology for protecting sensitive data from being intercepted by unauthorized parties.
How does TLS Encryption work?
TLS encryption works by establishing a secure connection between two parties, such as a web browser and a website. When a user accesses a website that uses TLS encryption, their browser and the website’s server negotiate a set of encryption protocols to use for communication. These protocols include key exchange methods, encryption algorithms, and message authentication codes. Once the protocols are agreed upon, the browser and server exchange digital certificates to verify each other’s identities.
Is TLS Encryption secure?
Yes, TLS encryption is considered to be secure when implemented properly. However, like any security measure, there is always a risk of vulnerabilities being discovered and exploited. It is important to keep TLS up to date and follow best practices for implementation to ensure the highest level of security.
What are the limitations of TLS Encryption?
There are some limitations to TLS encryption. It can add some overhead to the communication process, which can slow down the connection speed. Additionally, TLS encryption only protects the data while it is in transit between the client and server. Once the data reaches its destination, it may be vulnerable to other forms of attack. Finally, TLS encryption does not protect against all types of attacks, such as social engineering or phishing attacks.
What are the common attacks on TLS Encryption?
There are several common attacks on TLS encryption, including:
- Man-in-the-middle (MITM) attacks: An attacker intercepts the communication between the client and server and can view or modify the data being transmitted.
- DDoS attacks: An attacker floods the server with an overwhelming amount of traffic, causing it to become inaccessible to legitimate users.
- Session hijacking: An attacker steals the session ID of a user and uses it to impersonate the user and gain unauthorized access.
Where is TLS Encryption Used?
TLS encryption is commonly used in web browsing, email communication, instant messaging, and other forms of online communication to ensure that the data being transmitted is secure and cannot be intercepted or modified by unauthorized parties. It is also used in other applications that require secure communication, such as online banking and e-commerce transactions.
How do I implement TLS Encryption?
Implementing TLS Encryption requires a few steps:
- Obtain an SSL/TLS certificate: You can obtain a certificate from a trusted certificate authority (CA) or create a self-signed certificate.
- Install the certificate on your server: Once you have the certificate, you need to install it on your web server. This process varies depending on your server software.
- Configure your server: You need to configure your server to use HTTPS instead of HTTP.
What Are The Compliance Standards For TLS Encryption?
There are several compliance standards for TLS encryption, including:
- the Payment Card Industry Data Security Standard (PCI DSS): This standard requires that all payment processing systems use TLS encryption to protect sensitive data.
- Health Insurance Portability and Accountability Act (HIPAA): HIPAA requires that all electronic protected health information (ePHI) be transmitted securely using TLS encryption.
- General Data Protection Regulation (GDPR): The GDPR requires that all personal data be transmitted securely using TLS encryption.
What Is The Future Of TLS Encryption?
As technology continues to evolve, the future of TLS encryption will likely involve improvements in security and performance. This may include the development of new encryption algorithms or the optimization of existing ones to provide even stronger protection against cyber threats. Additionally, advancements in hardware and software may lead to faster and more efficient TLS encryption processes, enabling businesses to securely transmit data at even higher speeds. Overall, the future of TLS encryption looks promising as organizations continue to prioritize data security in an increasingly digital world.
