Introduction
Data encryption in transit is crucial to securing sensitive information while it is being transmitted over the internet. Malicious actors can intercept, read, and even modify data without proper encryption protocols. This can lead to serious consequences like identity theft, financial fraud, and data breaches. This article will offer an overview of some of the most popular encryption protocols used to protect data in transit, including SSL/TLS, IPSec, and SSH. By understanding how these protocols work, you can make informed decisions about protecting your data when transmitting it over the internet.
Define Data Encryption In Transit
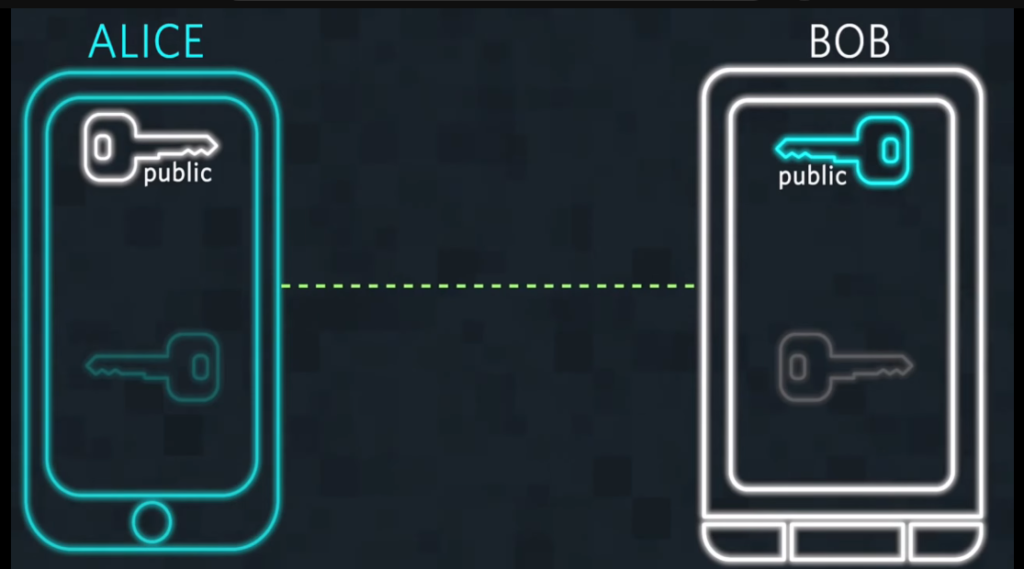
Data encryption in transit refers to encrypting data as transmitted between two devices or systems over a network, such as the internet. This protects the data from being intercepted, read, or modified by unauthorized parties. Encryption involves converting the original data into a code that can only be decoded by the intended recipient, who has the necessary decryption key. This ensures that even if the data is intercepted, it remains unreadable and secure. SSH is one of the protocols that can be used to encrypt data in transit.
Which Protocol Encrypts Data In Transit?
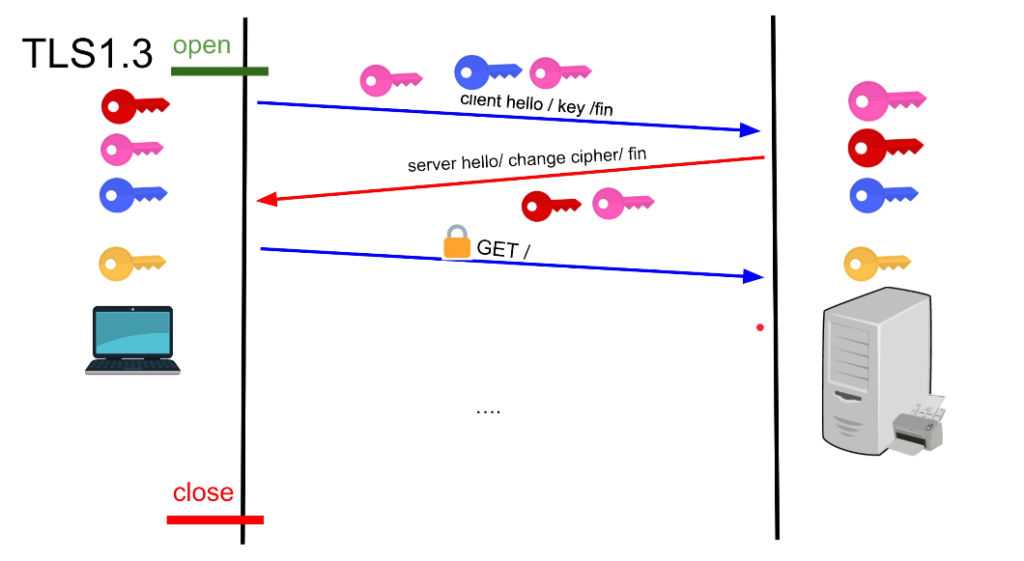
QUIC protocol encrypts data in transit by default using TLS 1.3 encryption, which provides end-to-end encryption and protects against eavesdropping and tampering.
What Is Data Transmission Encryption?
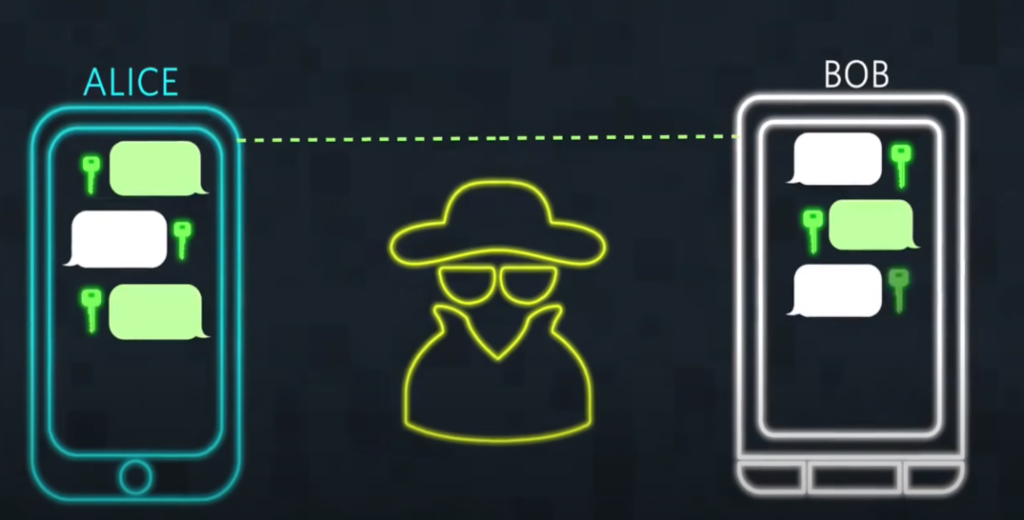
Data transmission encryption converts data into a code that can only be decoded by the intended recipient, who has the necessary decryption key, before transmitting it over a network like the internet. This ensures that even if the data is intercepted, it remains unreadable and secure. Encryption is an important security measure to protect sensitive information from being intercepted, read, or modified by unauthorized parties during transmission.
Decoding Data Encryption in Transit: An Overview of Popular Protocols
SSL/TLS
Explanation Of SSL/TLS Protocols
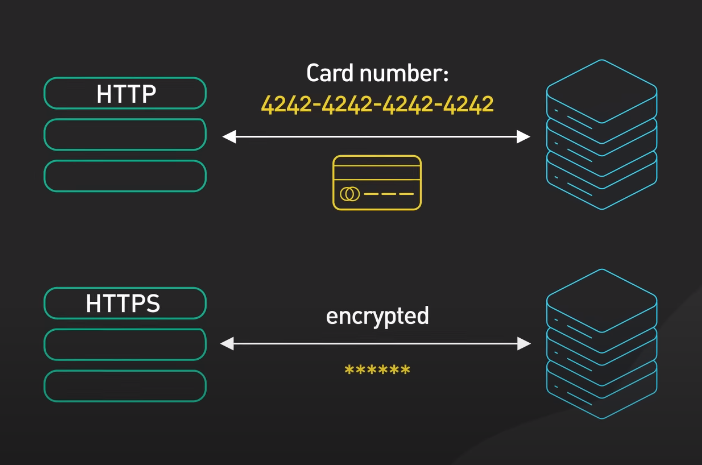
The SSL (Secure Sockets Layer) and TLS (Transport Layer Security) protocols are cryptographic protocols that secure internet communication. They provide a secure channel between two machines by encrypting the transmitted data. SSL/TLS protocols use symmetric and asymmetric encryption to secure the data. Symmetric encryption is used to encrypt the data that is being transmitted, while asymmetric encryption is used to create a protected connection between the two machines.
SSL/TLS protocols also use digital certificates to authenticate the identity of the server and the client. These certificates are issued by reliable third-party organizations called Certificate Authorities (CAs). The certificates contain information about the identity of the server or client and are used to verify that the machine is who it claims to be.
Difference Between SSL and TLS
SSL (Secure Sockets Layer) and TLS (Transport Layer Security) are protocols for securing internet communication. SSL was the first protocol developed for this purpose, while TLS is its successor. One of the main differences between SSL and TLS is their cryptographic algorithms. SSL uses 40-bit or 128-bit encryption, while TLS uses stronger algorithms such as 256-bit encryption. This makes TLS more secure than SSL.
Another difference is their compatibility with different web browsers. SSL is an older protocol not supported by some modern web browsers. TLS, on the other hand, is widely supported and is the recommended protocol for securing communication over the internet.
IPSec
It is important to note that implementing secure communication protocols, such as IPSec, can also help protect against these types of attacks. Additionally, regularly updating software and implementing proper security measures can help prevent vulnerabilities from being exploited.
Differences Between SSL/TLS And IPSec
SSL/TLS and IPSec are both protocols used for secure communication over the internet, but they have some differences:
- SSL/TLS is primarily used for securing web traffic, while IPSec can secure any network traffic.
- SSL/TLS operates at the application layer of the OSI model, while IPSec operates at the network layer.
- SSL/TLS combines public and symmetric key encryption, while IPSec only uses symmetric encryption.
- SSL/TLS is implemented at the application level, while IPSec is implemented at the operating system level.
SSH
SSH (Secure Shell) is a network protocol that permits secure communication between two networked devices. It is commonly used for remote login and secure file transfer. Some benefits of using SSH include:
- Encryption of all data transmitted between devices, providing strong security.
- Authentication of users and devices, ensuring that only authorized parties can access the network.
- Flexibility in configuration and management makes it suitable for various environments.
- Compatibility with a wide range of devices and software applications.
However, some potential drawbacks of SSH include:
- The need for proper configuration and management to ensure optimal security.
- The potential for increased latency due to the encryption and decryption process.
- additional hardware or software is needed to support certain encryption algorithms or protocols.
- Possible compatibility issues with some network devices or software applications.
- The need to use additional security protocols or technologies to ensure end-to-end security.
S/MIME
S/MIME (Secure/Multipurpose Internet Mail Extensions) is a protocol for securing email communication. It allows users to encrypt and digitally sign email messages, ensuring confidentiality and integrity. Email clients and servers widely support S/MIME and can be used with various keys, including RSA, DSA, and ECDSA. To use S/MIME, both the sender and recipient must have a valid S/MIME certificate issued by a trusted certificate authority. S/MIME is commonly used in businesses and organizations to protect sensitive email communication.
HTTPS
HTTPS (Hypertext Transfer Protocol Secure) is a protocol for secure communication over the internet. It encrypts the data transmitted between a user’s browser and a website, ensuring that sensitive information such as login credentials, credit card numbers, and personal information cannot be intercepted by hackers.HTTPS is becoming increasingly important as more and more users rely on the internet for sensitive transactions. Websites that handle sensitive information, such as banks, e-commerce sites, and social media platforms, should always use HTTPS to protect users.
A website must obtain an SSL/TLS certificate from a trusted authority (CA) to implement HTTPS. The certificate verifies the website’s identity and encrypts the data transmitted between the user’s browser and the website. Once the certificate is installed, the website will display a padlock icon in the browser’s address bar, indicating that the connection is secure.
DTLS
DTLS (Datagram Transport Layer Security) is a protocol that provides security for datagram-based applications such as Voice over IP (VoIP) and video conferencing. It is based on the TLS protocol and provides similar security features but is designed to work with unreliable datagram transport protocols such as UDP (User Datagram Protocol).DTLS provides encryption, authentication, and integrity protection for datagrams, ensuring they are not tampered with or intercepted by attackers. It also supports session resumption, allowing clients to resume a previously established session without re-establishing the connection.
One of the main benefits of DTLS is that it allows for real-time communication over unreliable networks, such as the internet. It can also be applied in scenarios where traditional TLS is unsuitable, such as IoT (Internet of Things) devices with limited processing power and memory.
PPTP
PPTP (Point-to-Point Tunneling Protocol) creates a virtual private network (VPN) over the internet. It is widely used for remote corporate network access and securing internet traffic.
Advantages:
- Easy to set up: PPTP is easy to set up and organize, making it a popular choice for small businesses and individuals.
- Compatibility: PPTP is supported by most operating systems, including Windows, Mac, and Linux.
- Speed: PPTP is known for its fast connection speeds, making it a good choice for applications that require real-time communication.
Disadvantages:
- Security: PPTP is considered less secure than other VPN protocols, as it uses weaker encryption algorithms and is vulnerable to attacks.
- Limited functionality: PPTP does not support advanced features such as multi-factor authentication, which can limit its usefulness in some applications.
- Firewall issues: PPTP can be blocked by some firewalls, which can cause connectivity issues.
L2TP/IPSec
Explanation Of L2TP/IPSec
L2TP/IPSec combines Layer 2 Tunneling Protocol (L2TP) and Internet Protocol Security (IPSec). L2TP is a tunneling protocol that allows virtual private networks (VPNs) creation. It does not provide any encryption on its own, but when combined with IPSec, it provides strong encryption and authentication for secure communication. IPSec is a suite of protocols that offers security services for IP networks. It provides confidentiality, integrity, and authentication for data transmitted over IP networks. When L2TP and IPSec are used together, L2TP provides the tunneling, and IPSec provides the security. This combination is commonly used for remote access VPNs and site-to-site VPNs. L2TP/IPSec is considered to be a secure and reliable protocol for VPNs, as it provides strong encryption and authentication, and most operating systems and VPN clients widely support it.
OpenVPN
What Is OpenVPN?
OpenVPN is a widely-used open-source VPN protocol that provides safe and reliable communication over the internet. It uses SSL/TLS encryption to ensure the confidentiality and integrity of data transmitted between the client and the server. OpenVPN is known for its flexibility and ease of use, and it can be used on various platforms, including Windows, macOS, Linux, Android, and iOS. It can also be configured to work with different network topologies, such as point-to-point, site-to-site etc.
OpenVPN Vulnerabilities
However, it is significant to note that, like any other technology, OpenVPN may have vulnerabilities that could compromise its security. It is always recommended to keep the software up-to-date and follow best practices for secure configuration and usage. Additionally, it is important to regularly monitor for any security advisories or updates related to OpenVPN.
IKEv2
IKEv2 (Internet Key Exchange version 2) is a VPN protocol known for its speed and security. Here are various advantages and disadvantages of using IKEv2:
Advantages:
- Fast: IKEv2 is known for its fast connection speeds, making it a great choice for users who need to quickly transfer large amounts of data.
- Secure: IKEv2 uses strong encryption algorithms and is considered very secure.
- Stable: IKEv2 is designed to be stable and reliable, making it a good choice for businesses or users who need a consistent connection.
- Mobile-friendly: IKEv2 is well-suited for mobile devices, as it can quickly reconnect to the VPN server after a connection is lost.
Disadvantages:
- Limited compatibility: While many devices and operating systems support IKEv2, it may not be compatible with older devices or some routers.
- Complex setup: Setting up IKEv2 can be more complex than other VPN protocols, which may be a barrier for some users.
- Limited customization: Unlike other VPN protocols, IKEv2 does not offer many customization options.
SSL VPN
- SSL VPN is a secure protocol that uses SSL encryption to provide remote access to a network. Routers and devices widely support it and are often used for remote work and telecommuting.
- SSL VPN vs. IPSec VPN: While SSL VPN and IPSec VPN are secure protocols, SSL VPN is generally easier to set up and use and is more widely supported by routers and devices. IPSec VPN, however, is often preferred for site-to-site VPN connections.
- SSL VPN vs. OpenVPN: OpenVPN is a highly configurable open-source protocol often used for remote access and site-to-site VPN connections. On the other hand, SSL VPN is easier to set up and use and is more widely supported by routers and devices.
- SSL VPN vs. PPTP: PPTP is an older VPN protocol generally less secure than SSL VPN. While PPTP may be faster, SSL VPN is more widely supported and provides better services.
QUIC
QUIC is a transport layer protocol developed by Google that aims to provide faster and more secure communication over the internet. Some benefits of QUIC include:
- Reduced latency: QUIC uses encryption and multiplexing to minimize the time it takes for a client to establish a connection with a server, resulting in lower latency.
- Improved reliability: QUIC includes built-in error correction and congestion control mechanisms, which can help improve the reliability of internet communication.
- Better security: QUIC uses TLS 1.3 encryption by default, which provides end-to-end encryption and protects against eavesdropping and tampering.
- Compatibility: QUIC is designed to work with existing internet infrastructure and is supported by most modern web browsers and servers.
Encrypted DNS
Encrypted DNS refers to using encryption protocols to protect the privacy and security of DNS queries and responses. This can be achieved through encryption technologies such as DNS-over-HTTPS (DoH) and DNS-over-TLS (DoT). Encrypted DNS helps prevent unauthorized access to DNS data, which can be used to track user activity and collect sensitive information.
Conclusion
Data encryption in transit is critical to online security, as it helps protect sensitive information from interception and unauthorized access. When choosing the right protocol for data encryption in transit, several factors come into play, including the level of security needed, the speed of data transfer, and compatibility with existing systems. One of the most popular protocols for data encryption in transit is Transport Layer Security (TLS), which is used to secure web traffic, email communication, and other online transactions. TLS uses symmetric and asymmetric encryption to protect data in transit, and web browsers, servers, and other online services have widely adopted it.
Another protocol gaining popularity for data encryption in transit is the encrypted Domain Name System (DNS). Encrypted DNS works by encrypting DNS queries, which translate domain names into IP addresses, making it more difficult for third parties to intercept and manipulate this information. Encrypted DNS can provide increased privacy and security for internet users, but it also has some drawbacks, such as increased latency, complexity, potential for abuse, and limited adoption.
Frequently Asked Questions (FAQs)
What Is The Best Data Encryption Protocol For My Website?
The best data encryption protocol for your website depends on your specific needs and requirements. Some commonly used encryption protocols for websites include HTTPS, SSL, and TLS. It’s important to consult a cybersecurity expert to determine the best encryption protocol for your website.
How Can I Tell If My Website Is Using An Encryption Protocol?
You can tell if your website uses an encryption protocol by checking the URL in the address bar. If the URL starts with “https” instead of “HTTP,” your website uses an encryption protocol. You can also check for a padlock icon in the address bar, indicating that the website is secure and using encryption.
How Does Data Encryption In Transit Differ From Data Encryption At Rest?
Data encryption in transit refers to encrypting data as it is transmitted between two devices or systems, such as a user and a server, over the internet. This is typically done to protect the data from being intercepted or modified by unauthorized parties during transmission. On the other hand, data encryption at rest refers to encrypting data stored on a device or system, such as a hard drive or database. This is typically done to protect the data from being accessed or stolen by illegal parties who gain physical or remote access to the device or system.
Both types of encryption are important for protecting sensitive data, but they serve different purposes and are implemented in different ways. Encryption in transit often involves using secure communication protocols such as HTTPS, SSL, or TLS. In contrast, encryption at rest may involve using encryption software or hardware to protect data stored on a device or system.
