Importance of Data Security In Modern Storage Facilities
Data security is of utmost importance in modern storage facilities. With the increasing reliance on digital storage and the exponential growth of data, it has become crucial to protect sensitive information from unauthorized access, theft, or loss. One key reason for the significance of data security is the potential financial and reputational damage that can result from a data breach. Companies that fail to adequately secure their data can face severe consequences, including legal liabilities, loss of customer trust, and damage to their brand image.
Potential Threats And Risks Associated With Data Storage
There are several potential threats and risks associated with data storage:
1. Unauthorized access: Hackers or unauthorized individuals gaining access to sensitive data can lead to data breaches and compromise the security of the information.
2. Data theft: Cybercriminals can steal sensitive data, such as personal information, financial records, or intellectual property, for their gain or to sell on the dark web.
Understanding Data Storage Facilities
Understanding the different types of data storage facilities is crucial for managing data effectively and mitigating risks. Here are some key considerations:
1. On-premises storage: This involves storing data within an organization’s physical infrastructure, such as servers and data centres. Risks associated with on-premises storage include physical theft, natural disasters, and hardware failures.
2. Cloud storage: Cloud service providers offer remote storage and computing resources.
3. Network-attached storage (NAS): NAS devices are dedicated file storage systems that connect to a network, allowing multiple users to access and share files. NAS offers centralized storage and data backup options.
4. Storage area network (SAN): SAN is a high-speed network that connects multiple storage devices to servers.
Physical Security Measures
Physical security measures are implemented to protect the physical infrastructure and assets of an organization. These measures include:
1. Access control systems: These systems restrict access to authorized personnel through methods such as key cards, biometric authentication, or PIN codes.
2. Video surveillance: This involves the use of cameras to monitor and record activities in and around the premises. It can act as a deterrent and provide evidence in the event of an incident.
Network Security Measures
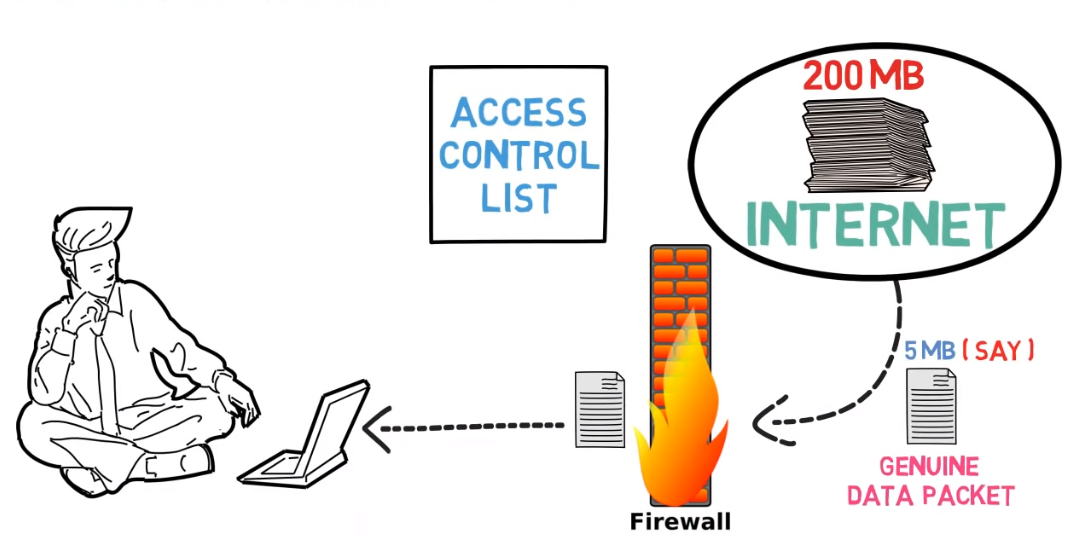
Network security measures are implemented to protect the organization’s digital assets and data. These measures include:
1. Firewalls: Firewalls are used to monitor and control incoming and outgoing network traffic. They act as a barrier between the internal network and external networks, preventing unauthorized access.
2. Intrusion Detection and Prevention Systems (IDPS): IDPS is designed to detect and prevent unauthorized access and attacks on the network.
Encrypting Data Transmissions And Communications
Encrypting data transmissions and communications is an important security measure to protect sensitive information from being intercepted or accessed by unauthorized individuals. Encryption converts data into a format that can only be deciphered with the appropriate encryption key, ensuring that even if the data is intercepted, it remains unreadable and secure.
Monitoring And Detecting Network Vulnerabilities
Monitoring and detecting network vulnerabilities is crucial for maintaining the security of a network. By regularly scanning the network for potential weaknesses, organizations can identify and address any vulnerabilities before they can be exploited by attackers. This includes conducting regular security audits, using intrusion detection systems, and implementing network monitoring tools to identify any suspicious activity or unauthorized access attempts. By staying vigilant and proactive in monitoring network vulnerabilities, organizations can better protect their data and systems from potential attacks.
Data Encryption and Backup Strategies
Data encryption and backup strategies are essential for organizations to protect their data from unauthorized access and potential loss. Encryption involves converting data into a coded form that can only be accessed with a decryption key. By encrypting sensitive data, organizations can ensure that even if it is intercepted or stolen, it cannot be read or used by unauthorized parties. Additionally, implementing regular data backup strategies is crucial for organizations to recover from potential data loss or system failures.
Choosing The Right Encryption Methods And Algorithms
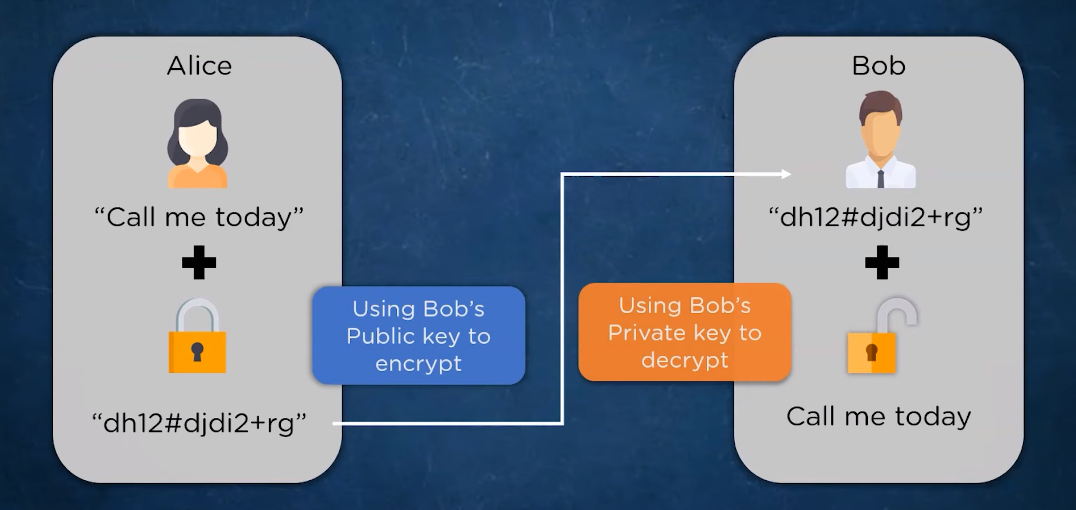
It is essential for ensuring the security of sensitive data. There are various encryption methods and algorithms available, such as symmetric encryption, asymmetric encryption, and hashing algorithms. Symmetric encryption uses a single key to both encrypt and decrypt the data. This method is efficient and fast but requires securely sharing the encryption key with authorized parties.
Asymmetric encryption, on the other hand, uses a pair of keys – a public key for encryption and a private key for decryption.
Regular Data Backups And Off-Site Storage
These are essential for ensuring data security and protection against data loss. Regular backups involve creating copies of important data and storing them in a separate location, such as an external hard drive or a cloud storage service. Off-site storage refers to keeping backups in a location that is physically separate from the original data, which provides an additional layer of protection in case of disasters or physical damage to the primary storage.
Physical Environmental Considerations
Physical environmental considerations are important for maintaining the integrity and longevity of data storage systems. Factors such as temperature, humidity, and power supply stability can impact the performance and reliability of storage devices. It is crucial to ensure that storage systems are kept in a controlled environment with proper cooling and ventilation to prevent overheating. Additionally, measures should be taken to protect storage devices from dust, moisture, and other potential hazards.
Temperature And Humidity Control
Temperature and humidity control are important for maintaining the integrity and longevity of data storage systems. Proper temperature regulation helps prevent overheating, which can lead to data corruption or even hardware failure. Similarly, controlling humidity levels helps prevent moisture buildup, which can cause damage to storage devices and lead to data loss. It is recommended to keep storage systems in a controlled environment with temperature and humidity monitoring and regulation systems in place.
Fire Prevention And Suppression Systems
Fire prevention and suppression systems are crucial for protecting data storage systems from potential fire hazards. These systems typically include fire alarms, smoke detectors, and fire extinguishers. They help to detect and suppress fires in their early stages, minimizing the risk of damage to the storage systems and the data they contain.
Data Destruction and Disposal
Data destruction and disposal are essential aspects of data security. When data storage systems reach the end of their lifecycle or when data is no longer needed, it is important to properly destroy and dispose of the data to prevent unauthorized access or data breaches. This process typically involves securely erasing or destroying the data, whether through physical destruction or digital wiping techniques. Proper data destruction and disposal procedures help to ensure that sensitive information does not fall into the wrong hands.
Employee Security Awareness

Proper data destruction and disposal procedures are crucial in maintaining data security and preventing unauthorized access or data breaches. When data storage systems reach the end of their lifecycle or when data is no longer needed6, it is important to follow appropriate measures to ensure the secure erasure or destruction of the data. Physical destruction methods involve physically destroying the storage media, such as hard drives, solid-state drives, or tapes.
Monitoring and Incident Response
Monitoring and incident response are integral components of an effective cybersecurity strategy. By continuously monitoring networks, systems, and applications, organizations can detect and respond to potential security incidents promptly. Monitoring involves the collection, analysis, and interpretation of various security-related data, such as logs, network traffic, and system events. This data is then used to identify anomalous or suspicious activities that may indicate a security breach or compromise.
Frequently Asked Questions (FAQs)
What are data storage facilities?
Data storage facilities are physical or virtual locations where data is stored and managed. These facilities can include on-premises data centres, cloud storage services, and other storage solutions. They provide the necessary infrastructure and resources to store and retrieve data securely and efficiently.
Why is data security important for storage facilities?
Data security is important for storage facilities because it helps protect sensitive and valuable information from unauthorized access, alteration, or loss. By implementing robust security measures, storage facilities can prevent data breaches, data leaks, and other security incidents that can lead to financial losses, reputational damage, and legal consequences. Data security also ensures compliance with relevant regulations and industry standards, which is crucial for businesses operating in various sectors.
How can physical security measures protect data storage facilities?
Physical security measures can protect data storage facilities in several ways:
1. Access control: Implementing access control measures, such as key card systems or biometric scanners, can restrict entry to authorized personnel only. This helps prevent unauthorized individuals from gaining physical access to data storage areas.
2. Perimeter security: Installing fences, gates, and surveillance cameras around the facility’s perimeter can deter and detect unauthorized access attempts. Additionally, security guards can be deployed to monitor the premises and respond to any suspicious activities.
What is the role of encryption in securing data storage?
The role of encryption in securing data storage is to protect the confidentiality and integrity of the stored data. Encryption involves converting the data into an unreadable format using an encryption algorithm and a unique encryption key. This ensures that even if unauthorized individuals gain access to the data storage, they will not be able to understand or manipulate the data without the encryption key. Encryption is an essential component of data security as it provides an additional layer of protection against unauthorized access and data breaches.
How often should data backups be performed?
Data backups should be performed regularly. The frequency of backups depends on the specific needs and requirements of the organization or individual. Generally, it is recommended to perform backups on a daily or weekly basis to ensure that the most up-to-date data is protected. Additionally, backups should be performed before any major system or software updates, as well as after significant data changes or additions.
How can organizations develop effective security policies?
Organizations can develop effective security policies by following these steps:
1. Identify and assess risks: Conduct a thorough analysis of potential security risks and vulnerabilities that the organization may face. This includes evaluating both internal and external threats.
2. Set clear objectives: Define the specific goals and objectives that the security policies should achieve. This could include protecting sensitive data, preventing unauthorized access, or ensuring compliance with industry regulations.
Conclusion
In conclusion, continuous monitoring is a crucial aspect of a robust cybersecurity strategy. It allows organizations to proactively identify and respond to potential security incidents, ensuring the protection of their networks, systems, and applications.
