There was a time and place when there was no such thing as insider threats, hacks, data theft and other similar threats. Let’s go back 60 years from now. Back then, there was no concept of using a computer to get things done. Be it at the workplace or at home, when you had to create a spreadsheet at work, it would have been made manually by hand and it took much longer. In regards to databases, files and folders were stored in filing cabinets, information was organized alphabetically so that it was easier to search for a particular file. For example, if an office administrator had to search a file on an individual, he or she would have to go into the filing room (in modern day, we would have server rooms) and if there are thousands of files, it could have taken a while to retrieve the information. Today, when it comes to making things easier, we can confidently say that computers have helped us become more productive and more efficient in managing our day to day tasks. We no longer have to rely on snail-mail to send letters. What’s more, take for example images, 60 years ago, we needed to have films developed on image paper, now there’s no need. We can simply save all of our images digitally on cloud storage for free. Next, look at videos, back in the days, if you needed to make a video, you needed to have a camcorder which would require a small video cassette, then that video had to recorded onto a larger cassette so that it could be viewed on a VCR player. Today, we are beyond such primitive technology. However, as we all know, everything in this world has flaws such as in the case of the proliferation of data theft due to the increase reliance on digital files.
Let’s face it, when it comes to keeping data secure, there’s no easy way. It seems like hackers and insiders are determined to steal personal information, be it personal images, videos, documents, files, folders, excel files, word files, access files or PDF files, you name it, they are after it. To make matters worse, many users are unaware of the fact that data needs to be safeguarded against hackers, crackers and insiders. Those who are not aware of such threats are often the ones on the losing end of the bargain.
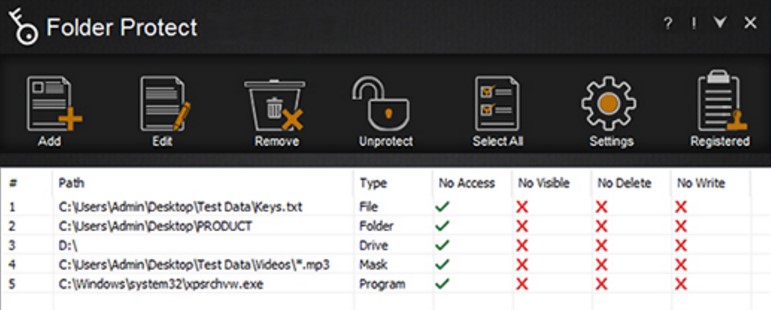
Today, there are many software programs that are designed to help people safeguard their personal data. However, most of them are not easy to use and are inflexible in terms of features and benefits. Nonetheless, Folder Protect is different, as it offers users the flexibility to protect their data how they want it. With Protect Folder, they can restrict files to be modified, they can prevent file deletion and they can lock and hide their files or folders completely. Folder Protect is a flexible data security software that caters to users with unique data security needs.
Should I Turn On Controlled Folder Access?

Yes, controlled folder access is a useful security feature that can help protect your system from malicious programs and ransomware. It is recommended that you turn it on if you are using Windows 10.
Things Happen If Turn Off Controlled Folder Access
If you turn off controlled folder access, your system will no longer be protected from malicious programs and ransomware. This means that your system will be more vulnerable to attacks and malicious software. It is recommended that you keep this feature enabled to protect your system from malicious programs and ransomware.
Folder Lock Be Hacked Or Not
Folder Lock can be hacked. Folder Lock is not a secure encryption method, and it is possible for a hacker to access the data stored in a Folder Lock folder. It is recommended that you use a more secure encryption method to protect your sensitive data.
Best Way To Protect System Files And Folders
The best way to protect your system files and folders is to use a strong password and enable two-factor authentication on your system. Additionally, you can use encryption to protect your data, and use an antivirus program to scan your system for any malicious software. It is also important to keep your operating system and applications up to date to ensure that any security vulnerabilities are patched.
Turn Off Ransomware Protection
Ransomware protection can be turned off by disabling it in your antivirus program. To do this, open your antivirus program and look for a setting that says “Ransomware Protection” or “Malware Protection”. Once you have found it, select the “Disable” option and save the changes. You may also need to restart your computer for the changes to take effect.
Turn On Ransomware Protection Windows 10
It is recommended to turn on ransomware protection in Windows 10. Ransomware is a type of malicious software that encrypts files on a computer and demands payment in order to unlock them. It is important to have ransomware protection in order to protect your files and data from being held hostage by cybercriminals.
Best Ways Of Protecting Files

1. Use a reliable antivirus software: Installing and regularly updating antivirus software can help protect your files from malicious software like ransomware.
2. Back up your files regularly: Backing up your files regularly can help protect them from being lost or damaged in the event of a ransomware attack.
3. Use strong passwords: Using strong passwords and two-factor authentication can help protect your files from unauthorized access.
Ways To Protect Stored Data
1. Use encryption: Encrypting your data can help protect it from unauthorized access.
2. Use secure cloud storage: Storing your data in a secure cloud storage system can help protect it from being accessed by unauthorized users.
3. Use secure file sharing: When sharing files, use secure file sharing protocols such as SFTP, FTPS, and HTTPS to help protect your data from unauthorized access.
4. Use strong passwords: Using strong passwords and two-factor authentication can
Most Secure Way To Store Files
The most secure way to store files is to use a combination of encryption, secure cloud storage, secure file sharing, and strong passwords. Encrypting your data helps protect it from unauthorized access, while secure cloud storage helps protect it from being accessed by unauthorized users. Secure file sharing protocols like SFTP, FTPS, and HTTPS help protect your data from unauthorized access, and strong passwords and two-factor authentication can help prevent unauthorized access to your data.
