
How To Use Flash Drives Without The Risk Of Data Leaks?
Using flash drives securely involves encrypting your drive with a strong password, regularly updating your antivirus software, and employing a ...
Read More
Using flash drives securely involves encrypting your drive with a strong password, regularly updating your antivirus software, and employing a ...
Read More
In our daily lives, we spend our times on different errands and forget what requires our utmost attention. Since the ...
Read More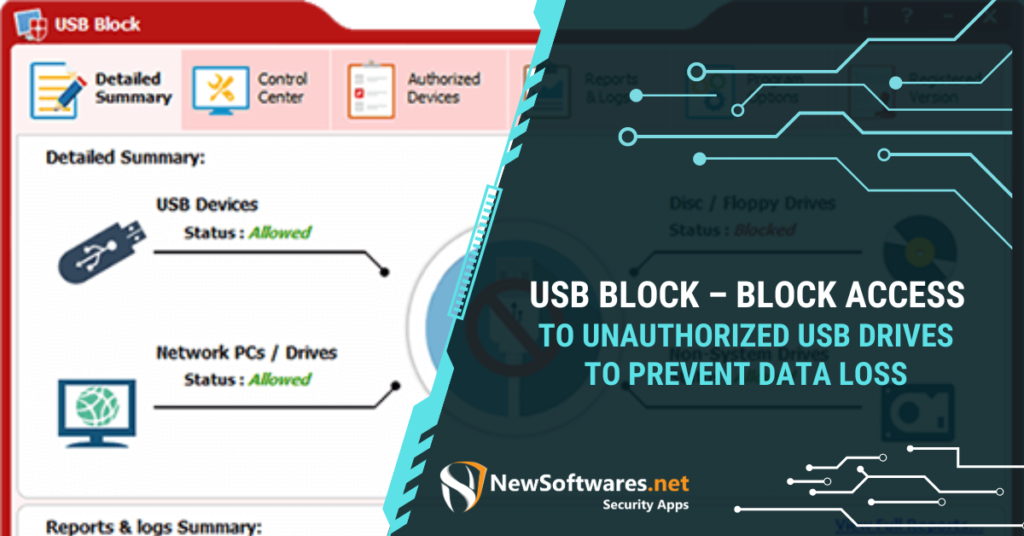
Consider yourself in a situation where you’re sitting with your friend and leave your PC/laptop under his supervision for a ...
Read More
Blessed we are to be born in such an era where life is too quick, fast, easy and enjoyable. Nowadays, ...
Read More
With the recent hacking of Yahoo servers, Information security experts are questioning yahoo’s cyber security practices. A second breach that ...
Read More
Most people, who hear about encryption, often express symptoms of confusion. They don’t know how encryption works. They know that ...
Read More
A nightmare is something that’s not real, but seems real because when you are dreaming, you are living it at ...
Read More
You arrive at your destination and park your car, you then put the car in park and remove the key ...
Read More
You are sitting on your computer, writing the final lines for your software code – yes, the one you’ve been ...
Read More
Organizations are built on ideas, and as we all know, ideas are hard to come by. Every organization has a ...
Read More
In a world full of digital technology – in other words, a world completely dependent on computer technology – will ...
Read More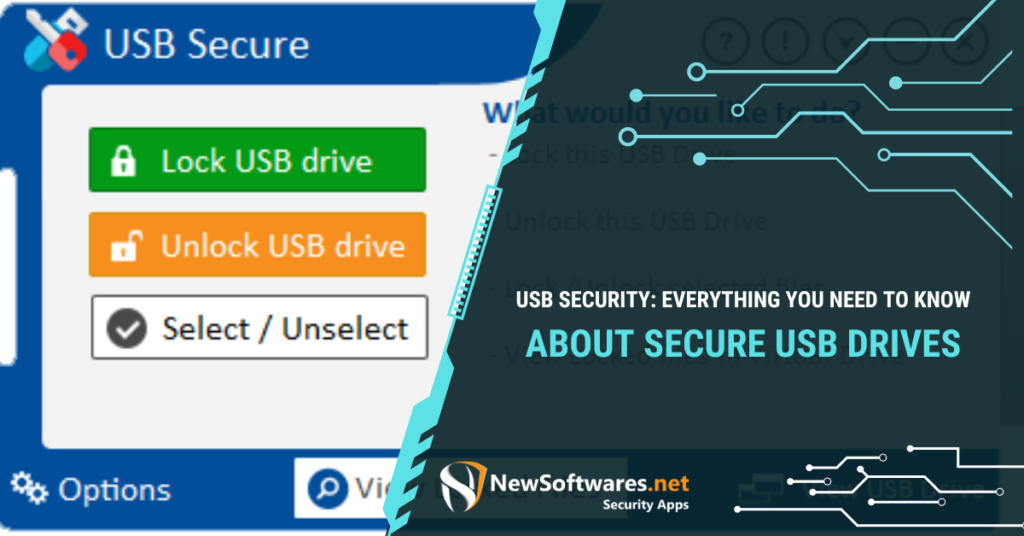
Many of you may have used USB flash drives at one point in your life, or you are an avid ...
Read More
This is a story of Mike and how he got away with stealing corporate data, given there wasn’t a USB ...
Read More
USB flash drives are small devices that allow you to store several gigabytes of data into a small device. Many ...
Read More
USB data storage devices are tiny, yet powerful and sturdy enough for everyday use, they are capable of storing information ...
Read More
Many people wonder why hackers do what they do? What value does stealing corporate data have for rogue employees – ...
Read More
If you are a small business owner, you are least likely to be concerned whether it would be beneficial for ...
Read More
Take that USB stick and shove it in your computer – it is that simple to transfer data from one ...
Read More
Personal Digital Assistant applications have become very essential for your android phones. Sometimes you are so much busy in your ...
Read More
One of the feature which has been continuously improving on smartphones is the camera. Nowadays, smartphones come loaded with different ...
Read More
Do you have some secret videos stored on your smartphone and you fear that they can be viewed by all? ...
Read More
So you’re like one of those people who have a really bad memory. You fail to reach appointments on time, ...
Read More
Google has announced in its blog post today that it is taking steps forward to protect users from embedded ads ...
Read More
So you’ve lost your android phone. It happens to everyone. It was just in your pocket a while ago, and ...
Read More
Changes made to Android up till January 15, 2016 In November 2014, Google hit a home run with the Android ...
Read More
Over the course of using your Android device, you’ve probably downloaded dozens of social media applications. Facebook, Twitter, Instagram, Skype, ...
Read More
The present day’s cybercriminals are armed and capable enough to carry out deadly cyber attacks on consumers, businesses and governments ...
Read More
In the late 90’s, desktop computers was the best tech marvel to hit the consumer electronic market. Back then, the ...
Read More
The Chinese government has passed a new law on data encryption, and yes it’s targeted towards security conscious Chinese users ...
Read More
This year is about to end and it hasn’t been a memorable year with respect to data security by any ...
Read More
Ever wonder what will happen if a database of a restaurant gets hacked? An American restaurant located in Daly City, ...
Read More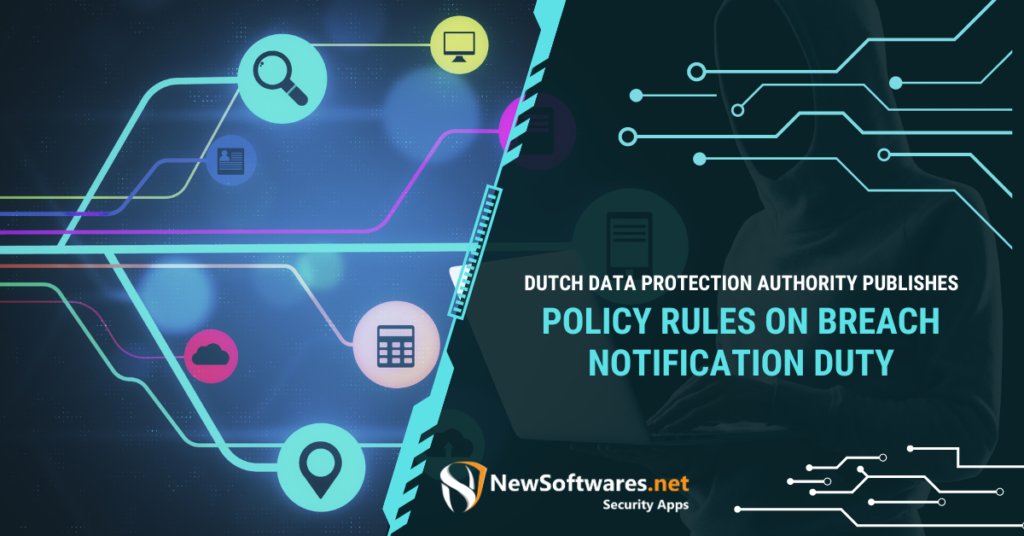
An amendment has been made to the Dutch Data Protection Act, which requires all data processors to notify Cbp of ...
Read More
Smartphones are the digital windows to our identities, thus they should be treated with utmost care and vigilance. Be it ...
Read More
Hackers proved this that hacking is not all about money. As a matter of fact, it would have been a ...
Read More
People do not like to keep the same model of smartphone for too long. They like to change it and ...
Read More
The year 2015 has been a nightmare for all smartphone users irrespective of the platform. In the mid of the ...
Read More
There are actually some typical types of smartphone users. You can be one of those that do not know much ...
Read More
Identity theft has become a severe problem for computer users all around the globe. The FBI (Federal Bureau of Investigation) ...
Read More
How to keep Data Safe and Secure? Whenever you try to read something about the progress or wonders of technology, ...
Read More
HP has been going through a management shuffle, now after sorting out all their shortcomings, the company has renewed its ...
Read More
Facebook is set to release a new tool which they call ‘Photo Magic’. It’s already out in Australia, where Facebook ...
Read More
The cloud computing industry is expected to expand at an exponential rate. The reason for that is, whether you are ...
Read More
The majority of the business goes through a difficult time when they experience a data breach incident. They leak sensitive ...
Read More
Data Security Data Security refers to the protection of data, such as a database, from the unwanted actions of unauthorized ...
Read More
Since the first text message was sent in 1992, it has become one of the most convenient form of communication. ...
Read More
When we think about hacking, we have this preconceived notion that someone far away is trying to access another person’s ...
Read More
Gone are the days of creating weak, ineffective passwords. The digital world is changing fast – and no – it’s ...
Read More
An all-inclusive guide on how to identify Android security problems and what you can do about it. How can you ...
Read More
Threats To Data Security It’s a well known fact that computer networks are riddled with problems. Accordingly, keeping them secure ...
Read More

Data Security and Encryption Softwares.