
Do All Apps Need A Privacy Policy, And How Much Data Should The App Be Allowed To Collect And Share
Yes, most apps need a privacy policy, especially if they collect any personal data from users. The extent of data ...
Read More
Yes, most apps need a privacy policy, especially if they collect any personal data from users. The extent of data ...
Read More
The Data-Driven Software Security Model is an advanced cybersecurity framework that uses data analytics, machine learning, and artificial intelligence to ...
Read More
The amount of data used by a security camera can vary depending on several factors, including the camera’s resolution, frame ...
Read More
Yes, HTTPS does encrypt data. It ensures the security and privacy of data during transmission over the internet. HTTPS encryption ...
Read More
The amount of data needed per month for security cameras varies based on several factors, including the camera’s resolution, frame ...
Read More
In today’s digital world, data is one of the most valuable assets for individuals and organizations. Keeping this information secure ...
Read More
In IPv6, the extension header used to encrypt data is the “Encapsulating Security Payload” (ESP) extension header. The Encapsulating Security ...
Read More
To secure your data on the cloud, it is important to take certain measures. Use strong authentication methods like passwords ...
Read More
In a PKI (Public Key Infrastructure) encryption method, the public key is used to encrypt the data. Data security has ...
Read More
To secure data at rest, it is crucial to encrypt the data, implement access controls, ensure physical security of storage ...
Read More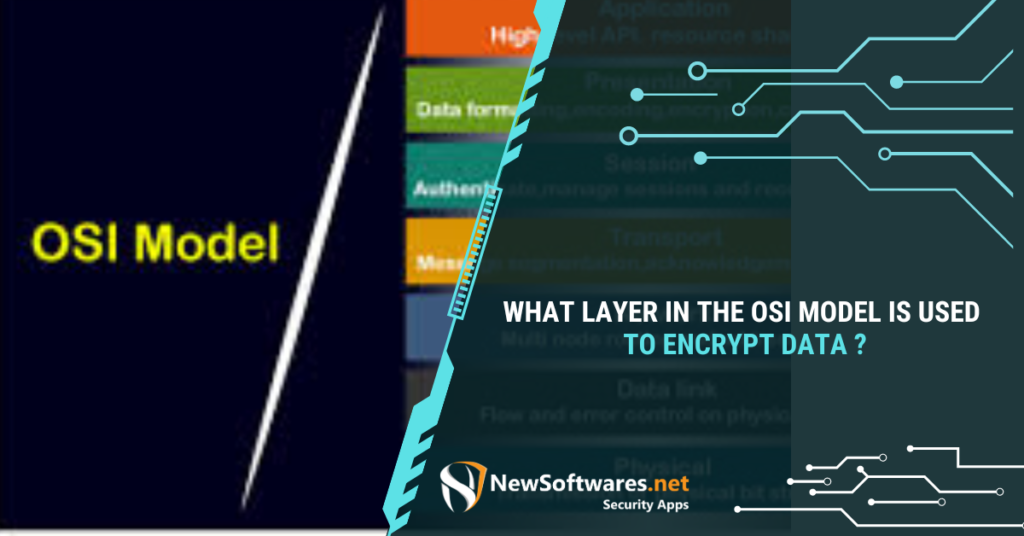
The layer in the OSI (Open Systems Interconnection) model used to encrypt data is the Presentation Layer. The Presentation Layer ...
Read More
Cellular data is generally more secure compared to open Wi-Fi networks. Cellular networks utilize encryption, authentication, and infrastructure security measures ...
Read More
In today’s fast-paced digital era, big data has emerged as a game-changer for businesses across various industries. The wealth of ...
Read More
To transfer data from an encrypted external hard drive to OneDrive, follow these steps: Decrypt the external hard drive using ...
Read More
Limit Access: Restrict HR data access to authorized personnel only. Use Encryption: Encrypt sensitive HR data in storage and transit. ...
Read More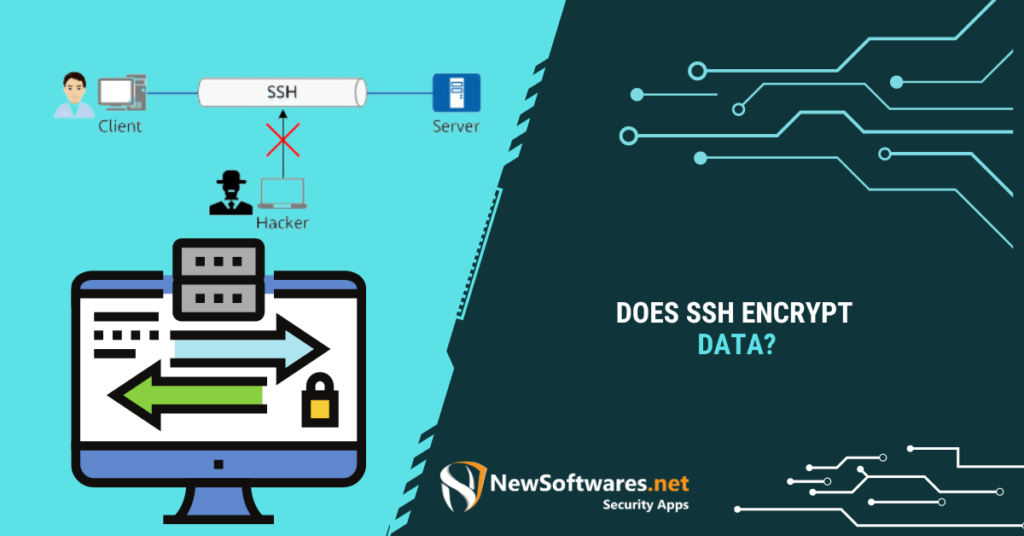
Yes, SSH (Secure Shell) encrypts data. SSH uses encryption algorithms to protect client and server data transmission. It achieves this ...
Read More
Choosing whether data science or cyber security is better depends on your personal interests, skills, and career goals. Both fields ...
Read More
The relationship between information securThe Regular Data Backupity and data availability is intertwined. Information security measures are crucial for maintaining ...
Read More
Insider Threats are the greatest threat to data theft in most secure organizations. In today’s digital landscape, data security is ...
Read More
In an era where data security is paramount, BitLocker drive encryption emerges as a powerful safeguard for protecting sensitive information. ...
Read More
End-to-End Encrypted Data on iCloud refers to a security measure implemented by Apple, where data remains encrypted throughout its entire ...
Read More
To assess the effectiveness of your encryption system, you can utilize various tools designed for this purpose. These tools are ...
Read More
Encryption is the process of converting data into an unreadable format, known as ciphertext, using an algorithm and a cryptographic ...
Read More
Asymmetric encryption is the type of encryption algorithm that uses 02(two) keys to encrypt and decrypt data. In the realm ...
Read More
To encrypt patient data, first assess which specific data needs encryption. Then, choose the appropriate encryption method, such as symmetric ...
Read More
To Protect your personal data in the digital age: update software, strengthen passwords, use VPNs, and minimize data exposure. In ...
Read More
In today’s digital age, data security is of utmost importance. With the increasing prevalence of cyber threats, protecting sensitive data ...
Read More
The organization or entity that collects, stores, processes, or handles the data is ultimately responsible for securing it. This responsibility ...
Read More
The cost of encrypting data can vary depending on several factors such as the specific encryption method used, the amount ...
Read More
To encrypt user data: Use a strong encryption algorithm like AES. Generate a unique encryption key for each user. Encrypt ...
Read More
The main goal of secure data destruction is to permanently and irreversibly remove sensitive or confidential information from storage devices ...
Read More
The Tor Browser indeed encrypts data to ensure your online activities remain private and secure. When you use the Tor ...
Read More
To encrypt JSON data in Java, you can use libraries like Javax.Crypto or Bouncy Castle. These libraries provide methods to ...
Read More
The amount of data a wireless security camera uses depends on several factors, such as the camera’s resolution, frame rate, ...
Read More
To copy data from a PDF file that is locked, follow these steps: Open the PDF file in Adobe Acrobat. ...
Read More
Dell Data Protection Security Tools refer to a comprehensive set of software solutions designed to safeguard sensitive data for businesses. ...
Read More
To encrypt data on your Android device, go to the Settings menu, locate the Security or Biometrics and Security option, ...
Read More
To encrypt data programmatically in Android, you can use the Android cryptographic APIs. These APIs provide various encryption algorithms and ...
Read More
The Security Master Data Management position role involves managing and maintaining the security-related data within an organization. In today’s rapidly ...
Read More
To remove Dell Data encryption from your computer, follow these steps: Obtain the Dell Data Security Uninstaller from the Dell ...
Read More
To decrypt encrypted data, you need to use encryption software or specialized tools. Install the chosen software, locate the encrypted ...
Read More
Securely backing up data involves implementing encryption, utilizing cloud storage or external drives, regularly updating backups, and verifying data integrity ...
Read More
A Social Security Number (SSN) is considered personally identifiable information (PII) and is classified as highly sensitive data. In today’s ...
Read More
Data security is one of the most critical aspects of any organization’s operations. In today’s digital age, where vast amounts ...
Read More
Yes, IPsec (Internet Protocol Security) encrypts data. It is a protocol suite used to secure communication over IP networks by ...
Read More
To Encrypt Data on Your Computer, Use built-in encryption features or third-party encryption software to encrypt data on your computer. ...
Read More
The Most secure way to prevent unauthorized access to your data is to use an end-to-end encrypted solution. With end-to-end ...
Read More
You can use the AES_ENCRYPT and AES_DECRYPT functions to encrypt and decrypt data in MySQL. To encrypt data, use the ...
Read More
In the digital age, privacy has become a significant concern. When using online services or browsing websites, knowing who has ...
Read More
The duration for which security cameras keep data typically ranges from 30 to 90 days, depending on factors such as ...
Read More

Data Security and Encryption Softwares.