How To Get Public Encryption Key?
How to Get Public Encryption Key? In this short guide, I’m going to give you the step-by-step instructions on how ...
Read MoreHow to Get Public Encryption Key? In this short guide, I’m going to give you the step-by-step instructions on how ...
Read More
Encryption is a vital cybersecurity technique that transforms readable data (plaintext) into an encoded form (ciphertext) using complex algorithms and ...
Read More
Encryption is vital in our digital age. It converts data into an unreadable code, protecting our privacy and security. It ...
Read More
Encryption involves converting data into an unreadable format to protect sensitive information from unauthorized access. You should use encryption in ...
Read More
Using encryption software is crucial to protect your privacy, secure sensitive information, and defend against cyberattacks. It ensures that your ...
Read More
Locking folders adds an extra layer of security, safeguarding financial records and personal documents. It also helps maintain an organized ...
Read More
End-to-end encryption (E2E) is a robust security protocol that ensures only the sender and intended recipient can read a message, ...
Read More
Folder encryption is a security technique that transforms the contents of a folder into an unreadable format, ensuring that unauthorized ...
Read More
Cellphone vulnerabilities refer to weaknesses in the security of mobile devices that can be exploited by malicious actors or software, ...
Read More
Tokenization and encryption are both vital data security techniques, each with its advantages and drawbacks. Tokenization involves substituting sensitive data ...
Read More
Encryption and decryption are essential tools for protecting data in the digital age. Encryption converts data into unreadable ciphertext, safeguarding ...
Read More
Encryption is a data security technique that converts readable data into an unreadable format using mathematical algorithms and a secret ...
Read More
Folder Lock is a user-friendly encryption and password protection software designed to safeguard your files, folders, and drives. It offers ...
Read More
Encryption converts readable data (plaintext) into an encoded form (ciphertext) using mathematical algorithms and cryptographic keys. Some of the best-paid ...
Read More
Using file and USB device encryption programs is crucial for safeguarding sensitive data in today’s digital world. File encryption protects ...
Read More
Encrypting your USB memory stick is crucial to provide robust protection against data loss and theft, a common risk due ...
Read More
No, encryption is not only for geeks. It’s a crucial part of our digital world, used by everyone to protect ...
Read More
Encryption is a powerful tool for data security with numerous merits. It safeguards stored data, allows centralized key management, secures ...
Read More
Introduction What Is Data Encryption? Data encryption refers to the process of converting plain text or data into a coded ...
Read More
Overview of Dell Data Protection Encryption Dell Data Protection Encryption is a comprehensive encryption solution that helps protect data on ...
Read More
Understanding Data Encryption Data encryption is the process of converting plain text into a coded or scrambled form, known as ...
Read More
Introduction A Brief Overview Of The Importance Of Data Encryption In The Digital Age Data encryption is a crucial element ...
Read More
Introduction Explanation Of What Data Encryption Is Data encryption is converting plain text into an unreadable format to protect the ...
Read More
Introduction Explanation Of Bluetooth Technology And Its Uses Bluetooth technology is a type of wireless communication that has been around ...
Read More
Introduction iCloud is a cloud storage and cloud computing service that was introduced by Apple Inc. in 2011. The service ...
Read More
Introduction Wireless network encryption is converting plain text data into a secret code to avoid unauthorized access to the network. ...
Read More
Introduction Data encryption in transit is crucial to securing sensitive information while it is being transmitted over the internet. Malicious ...
Read More
Introduction As more and more data is being stored in the cloud, the need for secure data storage and transmission ...
Read More
Intro to Dell Data Protection Encryption Dell Data Protection Encryption is software that provides data protection to your computer. It ...
Read More
Introduction What is Data Encryption? When we send or receive sensitive information, such as financial data or personal details, it’s ...
Read More
Introduction In today’s digital age, data security has become more important than ever before. As businesses and individuals increasingly rely ...
Read More
Importance of Phone Data Encryption In today’s digital age, our phones contain many sensitive information, including personal photos, financial information, ...
Read More
What is TLS Encryption? TLS (Transport Layer Security) encryption is a protocol that provides privacy and data integrity between two ...
Read More
Introduction Data transmission is a crucial aspect of modern communication and business operations. With the increasing reliance on technology, the ...
Read More
Data Encryption: An Overview Data encryption is the process of converting plain text or data into a coded format that ...
Read More
Importance of Data Security Data security is crucial in today’s digital age. With the increasing amount of sensitive information being ...
Read More
Significance of Data Encryption in VPNs Data encryption plays a crucial role in Virtual Private Networks (VPNs) as it ensures ...
Read More
Importance of Data Security in Databases Data security is a crucial aspect of databases as they store sensitive and confidential ...
Read More
The Ubiquity of FTP File Transfer Protocol (FTP) does not encrypt data by default, meaning that any data transferred using ...
Read More
Importance of VPN In Online Privacy A Virtual Private Network (VPN) is a service that allows you to create a ...
Read More
important of Encrypting Data in Excel Encrypting data in Excel is important because it helps protect sensitive information from unauthorized ...
Read More
Introduction Data encryption converts plain text or data into a coded form, which authorized individuals with the decryption key can ...
Read More
Introduction Data security is a vital aspect of any organization, and one of the most important components of data security ...
Read More
The importance of security in REST API Security is a critical aspect of any REST API implementation. REST APIs are ...
Read More
Definition of Data At Rest Encryption Data at rest encryption refers to the practice of encrypting data that is stored ...
Read More
Importance of SSL In Securing Online Communications SSL (Secure Sockets Layer) is a protocol that provides a secure and encrypted ...
Read More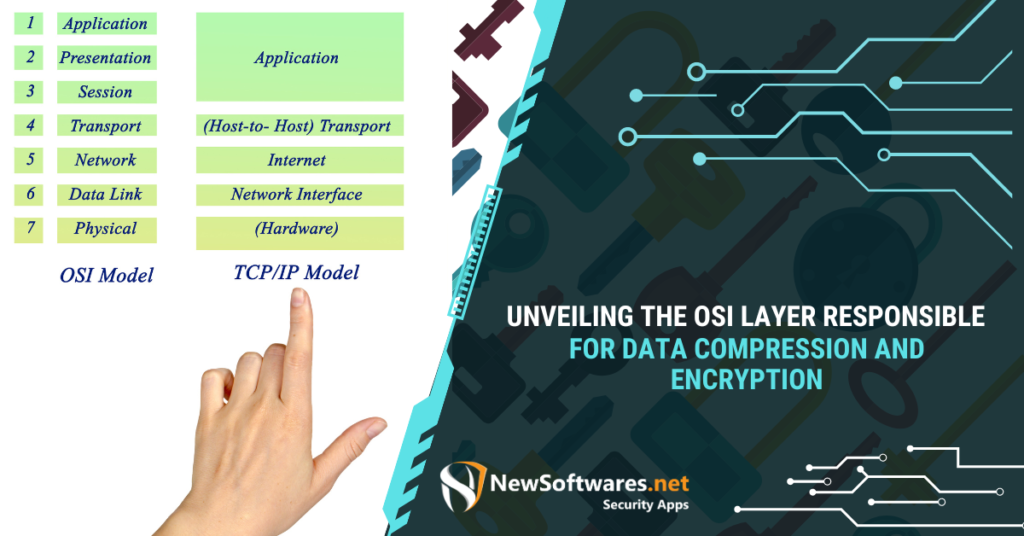
Overview of Data Compression And Encryption Data compression is the process of reducing the size of a file or data ...
Read More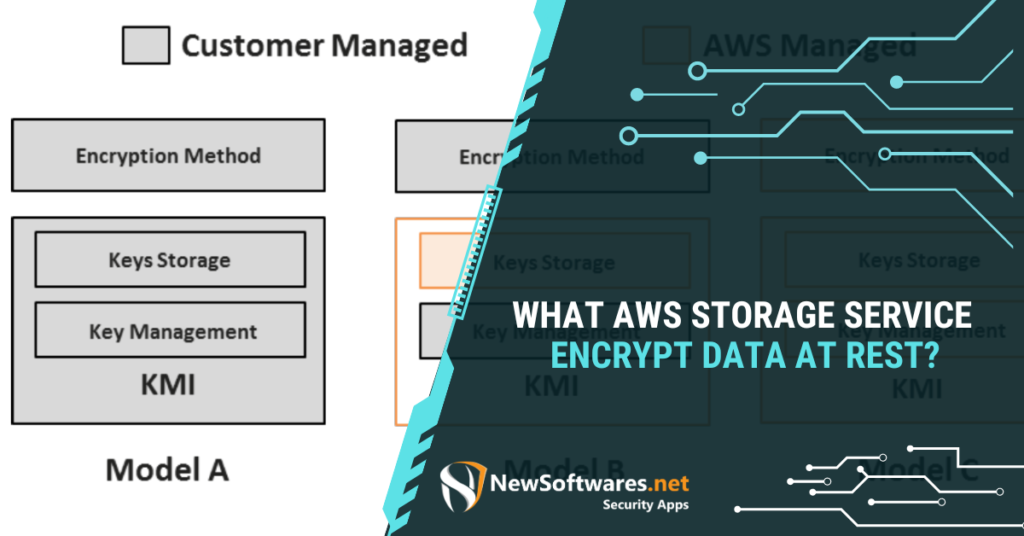
Your Ultimate Guide To AWS Storage Services: Which One Encrypts Your Data At Rest? Introduction AWS (Amazon Web Services) offers ...
Read More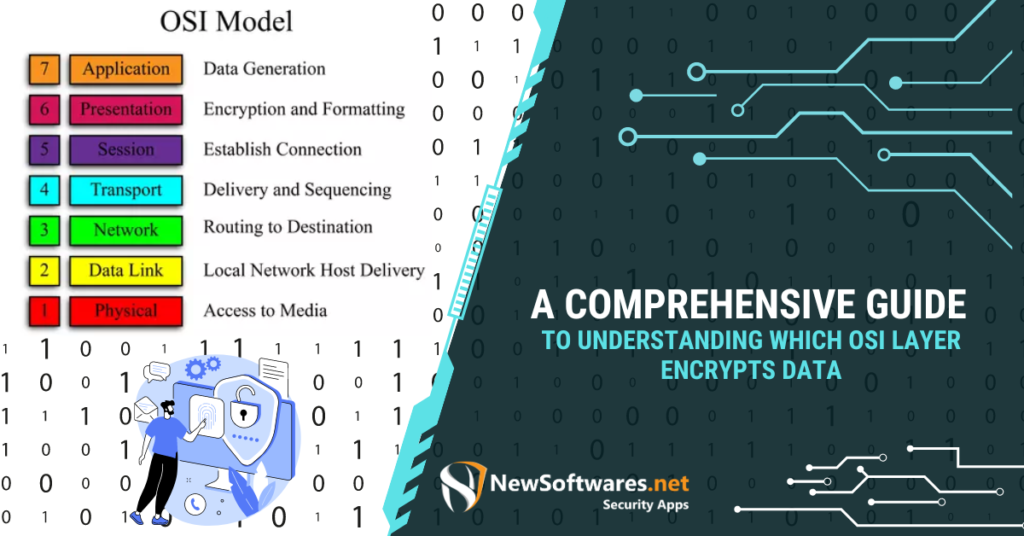
Overview of OSI Layers The OSI (Open Systems Interconnection) model is a conceptual framework that describes the communication functions of ...
Read More
Importance of Encryption in Protecting Data Encryption is a crucial tool for protecting data because it ensures that only authorized ...
Read More

Data Security and Encryption Softwares.