Understanding Data Encryption
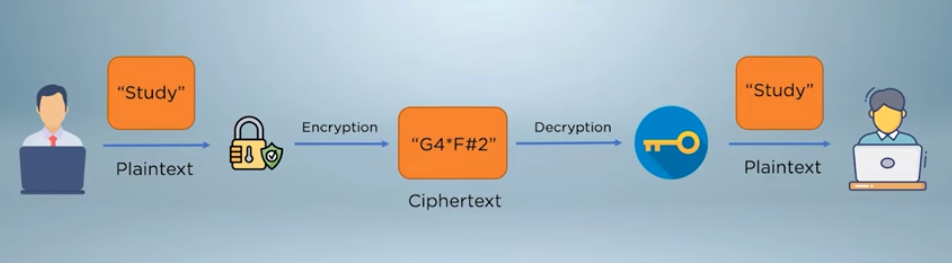
Data encryption is the process of converting plain text into a coded or scrambled form, known as ciphertext, to protect the confidentiality and integrity of the information. Encryption algorithms use mathematical formulas and keys to transform the data into an unreadable format that can only be decrypted by authorized parties who possess the corresponding decryption key. There are two main types of encryption: symmetric key encryption and public key encryption. With symmetric key encryption, the same key is used for both encryption and decryption.
Principles And Concepts of Encryption
Encryption is a process of converting plain text into ciphertext, which is a more secure form of data that can only be read by authorized parties. The main principles and concepts of encryption include confidentiality, integrity, and authenticity. Confidentiality refers to the protection of data from unauthorized access or disclosure. Encryption ensures that only authorized parties can access the data, as the ciphertext can only be decrypted with the corresponding decryption key.
Benefits And Challenges of Encryption
Encryption provides several benefits, including:
1. Security: Encryption ensures that data is secure and can only be accessed by authorized parties. This is particularly important for sensitive information such as financial data, personal information, and trade secrets.
2. Privacy: Encryption helps protect the privacy of individuals by ensuring that their data remains confidential.
3. Compliance: Encryption is often required by regulatory bodies and industry standards to protect sensitive data.
Identifying Sensitive Data

When it comes to identifying sensitive data, there are a few key factors to consider. First, consider the type of data you are dealing with. Financial data, personal information, and trade secrets are all examples of sensitive data that should be encrypted. Next, consider the potential impact of a data breach. If the data were to be compromised, what would be the consequences? Would it result in financial loss, reputational damage, or legal repercussions?
Defining Sensitive Data
Sensitive data can be defined as any information that, if disclosed, could cause harm or damage to an individual, organization, or entity. This can include personal information such as social security numbers, credit card information, and medical records, as well as confidential business information such as financial reports, trade secrets, and customer lists. Sensitive data can also include any information that is subject to regulatory compliance, such as HIPAA or GDPR.
Classifying Data Sensitivity Levels
Classifying data sensitivity levels is an important step in protecting sensitive information. The sensitivity level of data can be classified as low, medium, or high based on the potential harm or damage that could result if the information were to be disclosed. Low-sensitivity data includes information that is not confidential or private and does not pose a risk if disclosed. Examples of low-sensitivity data include public information such as company contact information, press releases, and marketing materials.
Assessing The Risks Associated With Sensitive Data
When assessing the risks associated with sensitive data, it’s important to consider the potential harm or damage that could result if the information were to be disclosed. This includes considering the impact on individuals, organizations, and society as a whole. For example, if high-sensitivity data such as personally identifiable information (PII) or financial information were to be disclosed, it could result in identity theft, financial fraud, or other serious consequences.
Securing Database Access
Securing database access is crucial in protecting sensitive data. One way to do this is by implementing strong authentication measures, such as requiring complex passwords and multi-factor authentication. It’s also important to limit access to the database to only those who need it and to regularly review and update access permissions as needed.
Establishing Strong Authentication Protocols
Establishing strong authentication protocols is essential for securing database access and protecting sensitive data. This can be achieved by implementing measures such as requiring complex passwords, enforcing password expiration and lockout policies, and implementing multi-factor authentication. Multi-factor authentication involves requiring users to provide two or more forms of identification before accessing the database.
Implementing Role-Based Access Controls
Another important measure for securing database access is implementing role-based access controls (RBAC). RBAC allows database administrators to assign specific roles to users, such as read-only or read-write access, based on their job responsibilities. This helps to ensure that users only have access to the information they need to perform their job functions and prevents unauthorized access to sensitive data.
Monitoring And Auditing User Activity
In addition to implementing RBAC, monitoring and auditing user activity is also crucial for securing database access. This involves keeping track of who is accessing the database, what actions they are taking, and when they are doing it. By monitoring user activity, administrators can quickly detect any suspicious behaviour and take appropriate action to prevent data breaches. Auditing user activity also helps to ensure compliance with regulatory requirements and provides a record of all database access for future reference.
Ensuring Data Recovery and Availability
To ensure data recovery and availability, it is important to have a backup and recovery plan in place. This involves regularly backing up the database and storing the backups in a secure location. In the event of a disaster or data loss, the backups can be used to restore the database to its previous state. It is also important to have measures in place to ensure the availability of the database.
Backup And Recovery Procedures
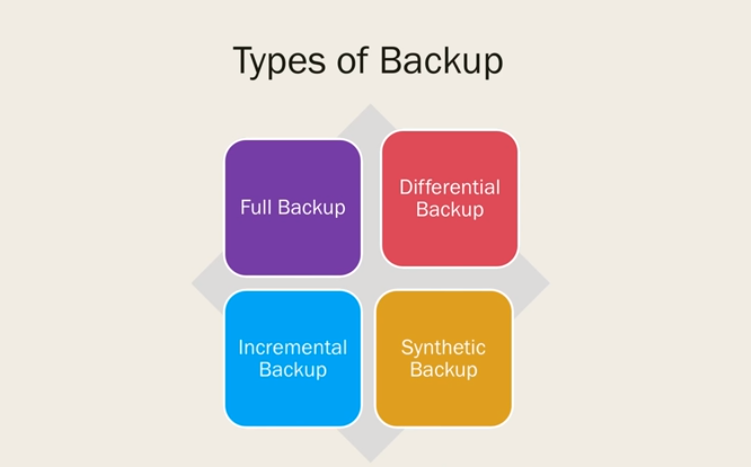
Backup and recovery procedures should be regularly tested to ensure their effectiveness. It is recommended to perform backup and recovery tests regularly to identify any potential issues and address them before they become a problem. Additionally, it is important to have a disaster recovery plan in place that outlines the steps to be taken in the event of a major disaster or outage. This plan should include procedures for restoring the database and ensuring its availability as quickly as possible.
High Availability Considerations
When it comes to high availability considerations for a database, there are several key factors to keep in mind. First, it is important to have redundancy built into the system, such as multiple servers or storage devices, to ensure that if one component fails, there is another one to take over. This can be achieved through clustering or replication technologies. It is also important to have monitoring and alerting systems in place to quickly identify any issues that may arise.
Disaster Recovery Planning
When it comes to disaster recovery planning for a database, it is important to have a backup strategy in place. This involves regularly backing up the database to a secure location, such as off-site storage or the cloud. It is also important to test the backup and restore processes to ensure they are working properly in the event of a disaster. Additionally, it is important to have a plan for restoring the database to a functional state as quickly as possible.
Conclusion
In conclusion, disaster recovery planning for a database is crucial for ensuring business continuity in the event of a disaster. By implementing a backup strategy, regularly testing the backup and restore processes, and having a plan for restoring the database, businesses can minimize the impact of a disaster on their operations.
